Writeup: DEF CON 2013 - Hypeman
Information
- Category: web
Writeup
Challenge was available at
http://hypeman.shallweplayaga.me where we found a login form:
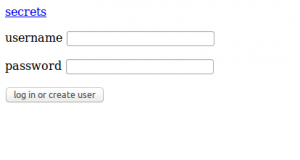
Clicking on Secrets link bring back to login so we tried to login as ZeroOFFset, getting to this page:
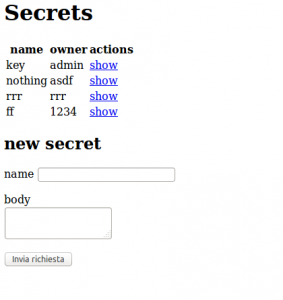
So we tried to see admin secret but an error occurred:

The error told has we were facing a ruby web application built upon Rack and the debug was enabled.
Looking at the error report we found some interesting stuff:
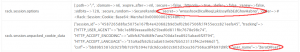
Moreover a piece of app source was displayed:
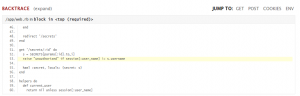
Maybe we can change the cookie to admin user and get through this error!
But it wasn’t so simple, the cookie was there, but it was encoded in some sort of base64 and an hash (the part after --):
1 | rack.session=BAh7CUkiD3Nlc3Npb25faWQGOgZFRiJFNDU4NzI2NWQ4ZmFjNTA3NWUxNjdm%0AYjRlNDIwNjgyYjlkM2VmMDJiNjc1MDZmYzFmNDU1ZWNjYzgyMWVlZmE0NUki%0ADXRyYWNraW5nBjsARnsISSIUSFRUUF9VU0VSX0FHRU5UBjsARiItYjhjMWU4%0AZjg5ZWVhZWEwYjgyNWJlZDBkODExZjBjNzY3OGU5OGM3NEkiGUhUVFBfQUND%0ARVBUX0VOQ09ESU5HBjsARiItYTBiZmM4NzZkNjhmZTdhZWE3MDBkYTVlYTg5%0AMjVhYmFjNmYyZjc5NEkiGUhUVFBfQUNDRVBUX0xBTkdVQUdFBjsARiItMzVh%0AOWFkZmM2MmIyYWRhNjUzZTA2N2JiNTIzMTMzZjRjMmU5NjZkMUkiCWNzcmYG%0AOwBGIkViYjg5YjUzODFkYzkyNWY5YjdjOTdiMzk0ZTdkYzlkY2NlYjAyYzYw%0AM2QzY2VhMzY3NTY2YWM4ZjRiOTdkOWZjSSIOdXNlcl9uYW1lBjsARkkiD1pl%0Acm9PRkZzZXQGOwBU%0A--943fba10b684ed09bcb7d9ee151262b0d18bbe16 |
Rack is an open source project so we looked for the source code handling the cookies, and we found it on github.
Looking at those sources we built this script that take the base64 encoded part of a cookie and creates a new one with user_name set toadmin:
1 | require 'rack' |
The secret needed to create the hash was displayed in plaintext in the debug report, as highlighted previously.
So we copied the cookie created by the application when we logged in as ZeroOFFset, we replaced <your cookie goes here> in the script above
with the base64 part of the cookie and we completely replaced the cookie with the one generated by the script.
And here it is the key!
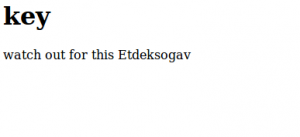
Flag
1 | Key FOUND: watch out for this Etdeksogav |