- category: Forensics/Steganography
- points: 75
Description
Caasi Vomisa built a bunker years ago because he already knew mankind was too dumb not to use nuclear warheads.
Today he is testing it again because he fears Pmurt or Nitup could push the wrong button on their coffee machines.
He was testing the bunker radio receiver when he received a strange transmission…
Can you help him find out what the transmission is about ?
Flag Format: INSA{...}
Source: find_me.unk
Writeup
This challenge was resolved as an exercise during a weekly meeting.
file find_me.unk
find_me.unk: JPEG image data, JFIF standard 1.01, aspect ratio, density 72x72, segment length 16, Exif Standard: [TIFF image data, big-endian, direntries=7, orientation=upper-left, xresolution=98, yresolution=106, resolutionunit=2, software=Pixelmator 3.4.2, datetime=2016:02:08 13:02:40], baseline, precision 8, 700x500, frames 3

Investigation
Let’s try to check if hidden files are embedded in the JPEG using trid or binwalk.
trid:
1
2
3
4
5
6
7
8
9
| TrID/32 - File Identifier v2.24 - (C) 2003-16 By M.Pontello
Definitions found: 9852
Analyzing...
Collecting data from file: find_me.unk
38.4% (.JPG) JFIF-EXIF JPEG Bitmap (5000/1/1)
30.7% (.JPG) JFIF JPEG bitmap (4003/3)
23.0% (.JPG) JPEG bitmap (3000/1)
7.6% (.MP3) MP3 audio (1000/1)
|
binwalk:
1
2
3
4
5
6
7
8
9
10
11
12
| Scan Time: 2018-04-23 22:36:26
Target File: /home/dodo/Desktop/forensics/find_me.unk
MD5 Checksum: a22cbaa5ccf854fdaa83445c71a34604
Signatures: 344
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
30 0x1E TIFF image data, big-endian, offset of first image directory: 8
399 0x18F Unix path: /www.w3.org/1999/02/22-rdf-syntax-ns#"> <rdf:Description rdf:about="" xmlns:xmp="http://ns.adobe.com/xap/1.0/" xmlns:dc="http://
38708 0x9734 PNG image, 627 x 357, 8-bit/color RGBA, non-interlaced
38807 0x9797 Zlib compressed data, best compression
|
Using foremost -a -v we can extract the embedded PNG: an image of a morse dictionary.
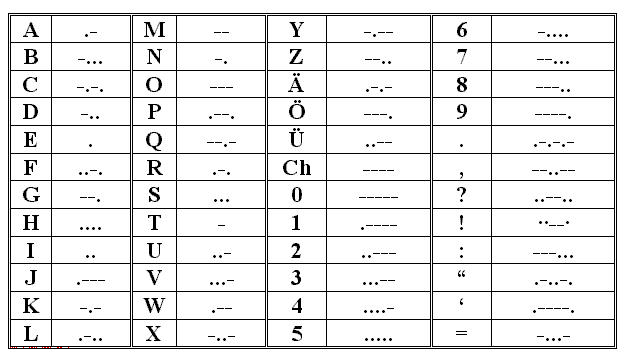
But…Where is the encoded morse code?
TrId found a 7.6% of MP3 audio so we thought to see for an hidden audio file in the images.
Using hexdump -C we saw, at the of the file, something familiar…
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
| 00035590 30 01 24 cf 37 56 83 df ea 5b b1 89 44 00 60 f7 |0.$.7V...[..D.`.|
000355a0 98 47 e9 ba 7d e3 f1 04 fd 76 ff c3 5a 93 a5 94 |.G..}....v..Z...|
000355b0 5c 98 81 73 37 12 06 13 ff 00 34 e7 d5 c3 eb ae |\..s7.....4.....|
000355c0 74 5f 75 00 48 00 00 00 90 18 c9 2a 77 14 22 59 |t_u.H......*w."Y|
000355d0 7c 9d 3e 8e 01 4c ef 37 7b 76 a4 61 ff 54 25 00 ||.>..L.7{v.a.T%.|
000355e0 40 00 00 00 c0 aa 68 e8 84 de 9d 46 02 9a da 9e |@.....h....F....|
000355f0 ad b7 14 e3 ec ff ef 0d 5b 18 38 18 9f 7c da 9d |........[.8..|..|
00035600 b7 c7 18 63 fc f8 33 10 00 00 00 00 00 00 00 00 |...c..3.........|
00035610 00 00 00 3b bc 65 3e 7d 6f c8 58 be d1 da f7 fd |...;.e>}o.X.....|
00035620 df 68 4d 00 be da 5e a6 b7 7f 60 ce 6f 84 79 f2 |.hM...^...`.o.y.|
00035630 c0 34 00 c0 a7 15 00 00 00 00 00 00 00 00 00 00 |.4..............|
00035640 00 00 c0 ce 34 dc 9c 59 02 00 bb e8 01 00 00 00 |....4..Y........|
00035650 be da 5e 8e b7 5f 90 ce ef 11 e6 06 2c 01 00 00 |..^.._......,...|
00035660 00 00 00 00 00 00 00 00 00 00 00 00 7f 7d 04 00 |.............}..|
00035670 00 00 00 c0 60 ee 7a 2e 00 00 00 00 be da 5e b6 |....`.z.......^.|
00035680 6f bf a0 9d 1f 03 cc 1d 98 06 00 f8 f4 01 00 00 |o...............|
00035690 00 00 00 00 00 00 00 00 00 00 00 40 1d cd 02 00 |...........@....|
000356a0 f8 46 2f 00 00 00 00 be da 5e f6 b7 3f 90 ce ef |.F/......^..?...|
000356b0 06 73 07 96 00 00 00 00 00 00 00 00 00 00 00 00 |.s..............|
000356c0 00 00 80 3f 3e 03 00 00 00 00 a0 9d 39 ac 0a 00 |...?>.......9...|
000356d0 00 00 be da 5e 8e b7 5f 50 ce ef 08 73 07 a6 01 |....^.._P...s...|
000356e0 00 ee b6 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000356f0 00 a0 aa 12 00 b8 5e 07 00 00 00 00 be da 5e 8e |......^.......^.|
00035700 b7 5f 50 ce ef 06 73 05 2c 01 00 00 00 00 00 00 |._P...s.,.......|
00035710 00 00 00 00 00 00 00 00 7f 7d 04 00 00 00 00 c0 |.........}......|
00035720 e2 af f3 e5 01 00 00 00 be da 5e f6 b7 3f 90 ce |..........^..?..|
00035730 ef 06 73 05 4c 03 00 9c 2d 00 00 00 00 00 00 00 |..s.L...-.......|
00035740 00 00 00 00 00 00 00 90 d0 14 00 40 a6 5e 00 00 |...........@.^..|
00035750 00 00 be da 5e 8e b7 5f 50 ce ef 08 73 07 96 00 |....^.._P...s...|
00035760 00 00 00 00 00 00 00 00 00 00 00 00 00 80 7f fe |................|
00035770 02 00 00 00 00 c0 e4 e0 f4 0a 00 00 00 00 be da |................|
00035780 5e 8e b7 5f 50 ce ef 01 e6 0e 4c 03 00 54 2d 00 |^.._P.....L..T-.|
00035790 00 00 00 00 00 00 00 00 00 00 00 00 00 b4 aa 97 |................|
000357a0 00 80 7e 7d 00 00 00 00 be da 5e 8e b7 5f 50 ce |..~}......^.._P.|
000357b0 ef 06 73 05 2c 01 00 00 00 00 00 00 00 00 00 00 |..s.,...........|
000357c0 00 00 00 00 7f bd 03 00 00 00 00 60 f1 a7 3e 2c |...........`..>,|
000357d0 00 00 00 00 4f 67 67 53 00 04 fc 07 24 00 00 00 |....OggS....$...|
000357e0 00 00 81 70 d4 52 1b 00 00 00 a6 a7 e3 cd 23 2a |...p.R........#*|
000357f0 4c a8 85 01 01 01 01 01 01 01 01 01 01 01 01 01 |L...............|
00035800 01 01 01 01 01 01 01 01 01 01 01 01 01 01 01 01 |................|
00035810 01 01 be da 5e f6 b7 3f 90 ce 4f 83 79 f4 c0 34 |....^..?..O.y..4|
00035820 00 c0 34 02 00 00 00 00 00 00 00 00 00 00 00 00 |..4.............|
00035830 00 04 08 65 00 00 4b 24 00 00 00 00 5e 9a 5e f8 |...e..K$....^.^.|
00035840 a7 14 53 62 ff 42 3a 5c 8e c8 a0 5e f4 fc 2f 7c |..Sb.B:\...^../||
00035850 ab 48 00 c0 88 88 00 00 00 00 00 a0 68 ba a4 67 |.H..........h..g|
00035860 9a 9d f7 4f 31 c7 4d 28 6f 2a a8 00 03 21 5f d9 |...O1.M(o*...!_.|
00035870 1c 27 d8 70 0a 8a 61 48 45 03 ee 6d f3 40 ba 32 |.'.p..aHE..m.@.2|
00035880 1e bd 61 da a6 03 3c 00 7e 96 74 ca eb 23 71 1e |..a...<.~.t..#q.|
00035890 50 42 27 e3 7a 22 57 ea 94 fa fe 64 67 1b c9 02 |PB'.z"W....dg...|
000358a0 d2 18 81 a7 24 46 60 ff 79 59 c3 5a da cc f2 fd |....$F`.yY.Z....|
000358b0 59 97 bd 25 27 e3 98 26 3e 13 6b 7f 89 1e b6 20 |Y..%'..&>.k.... |
000358c0 12 36 47 ab 5b 84 48 3f b3 62 65 39 d9 b3 cc 83 |.6G.[.H?.be9....|
000358d0 2c eb 55 54 dd 82 48 d0 a5 65 33 61 26 cb 16 04 |,.UT..H..e3a&...|
000358e0 15 fb 02 dc 58 32 61 f6 62 4e a6 c1 19 4e cf c7 |....X2a.bN...N..|
000358f0 82 15 a2 2d e8 89 01 d0 f1 3f d1 02 2d eb b2 d8 |...-.....?..-...|
00035900 1e a2 0c fb 99 c1 f3 c1 3e 9d f2 11 08 f9 38 e6 |........>.....8.|
00035910 a6 b0 6d b1 be 2c 13 8e 53 c8 78 e6 68 6a 97 b3 |..m..,..S.x.hj..|
00035920 10 b4 eb 5d 20 a2 1b f2 dd c1 51 a0 81 af 01 1a |...] .....Q.....|
00035930 fe 95 bc b8 cb 3f 1d 71 44 4c 51 e4 87 03 8c 01 |.....?.qDLQ.....|
00035940 63 0c cc 73 00 48 75 89 99 41 09 06 00 00 50 6e |c..s.Hu..A....Pn|
00035950 7a 06 0f c7 55 2a 7b 4a 6b ed 1b e0 2d c4 61 54 |z...U*{Jk...-.aT|
00035960 13 ea 02 e5 80 ad b4 10 e0 85 e6 92 c2 c7 9c 3c |...............<|
00035970 c3 32 cb ef 1f 3a 6e 54 8f 5e 9f 1c 31 9a 3b 46 |.2...:nT.^..1.;F|
00035980 ab b3 ab a8 af b2 f0 41 33 db b2 59 3b 3f 04 6c |.......A3..Y;?.l|
00035990 67 7f b4 64 58 62 37 1e f1 0e 98 1f 1f a2 25 03 |g..dXb7.......%.|
000359a0 ee 68 d6 77 01 3c 3a 1f 4e 27 2f e9 12 92 07 00 |.h.w.<:.N'/.....|
000359b0 4b c9 b0 04 12 0e 0e 0e 0e 0e 0e 0e 0e 0e 0e 0e |K...............|
000359c0 0e 0e 0e 0e 0e 0e 0e 0e 0e 0e 0e 0e 0e 0e 0e 0e |................|
000359d0 0e 0e 0e 0e |....|
000359d4
|
From wikipedia the EOF of a JPEG should be FF D9 but there is not such a thing at the end; BUT is it clearly visible a OggS chunk!
https://en.wikipedia.org/wiki/List_of_file_signatures OGG magic byte is 4f 67 67 53 which is OggS: maybe there is an audio track at the end of the file.
Previous tools did not recognized this signature (tool or our fault?) so the best way is to extract bytes using python:
1
2
3
4
5
6
7
| with open("sources/find_me.unk", "rb") as inputf, open("new.ogg", "wb") as outputf:
data = inputf.read()
offset = data.find(b"\x4f\x67\x67\x53")
print("OFFSET: ", offset)
inputf.seek(offset)
dataogg = inputf.read()
outputf.write(dataogg)
|
OggS in hex is \x4f\x67\x67\x53.
new.ogg: Ogg data, Vorbis audio, mono, 44100 Hz, ~80000 bps, created by: Xiph.Org libVorbis I
Let’s open it with audacity!
GREAT! We have a nice audio track with some beeps! That’s the morse code!
After OGG extration using audacity we can plot a morse text:
.. -. ... .- -.--. -- ----- .-. ..... ...-- ..--.- .-- .---- .-.. .-.. ..--.- -. ...-- ...- ...-- .-. ..--.- ....- --. ...-- -.-.-- -.--.-
First try decoding using an online converter: INSA<KN>M0R53#W1LL#N3V3R#4G3#)
Not so great…maybe the first image was useful to map some symbols in the flag to the correct morse code; MAYBE :)!
Nope: INSA # M0R53 # W1LL # N3V3R # 4G3! # (# is used with an unknown symbol).
The flag format is useful to search online morse code for {,} and some other symbols used on CTF flags (_, !, @, etc.).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
| import sys
coding_table = {
".-": "A",
"-...": "B",
"-.-.": "C",
"-..": "D",
".": "E",
"..-.": "F",
"--.": "G",
"....": "H",
"..": "I",
".---": "J",
"-.-": "K",
".-..": "L",
"--": "M",
"-.": "N",
"---": "O",
".--.": "P",
"--.-": "Q",
".-.": "R",
"...": "S",
"-": "T",
"..-": "U",
"...-": "V",
".--": "W",
"-..-": "X",
"-.--": "Y",
"--..": "Z",
"-----": "0",
".----": "1",
"..---": "2",
"...--": "3",
"....-": "4",
".....": "5",
"-....": "6",
"--...": "7",
"---..": "8",
"----.": "9",
"-.--.": "{",
"-.--.-": "}",
".--.-.": "@",
".-.-.-": ".",
"--..--": ",",
"-.-.-.": ";",
"..--..": "?",
"-.-.--": "!",
"-....-": "-",
"..--.-": "_",
}
morse = ".. -. ... .- -.--. -- ----- .-. ..... ...-- ..--.- .-- .---- .-.. .-.. ..--.- -. ...-- ...- ...-- .-. ..--.- ....- --. ...-- -.-.-- -.--.-"
for i in morse.split(" "):
try:
sys.stdout.write(coding_table.get(i))
except:
sys.stdout.write(" # ")
print()
|
Flag
INSA{M0R53_W1LL_N3V3R_4G3!}
