1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
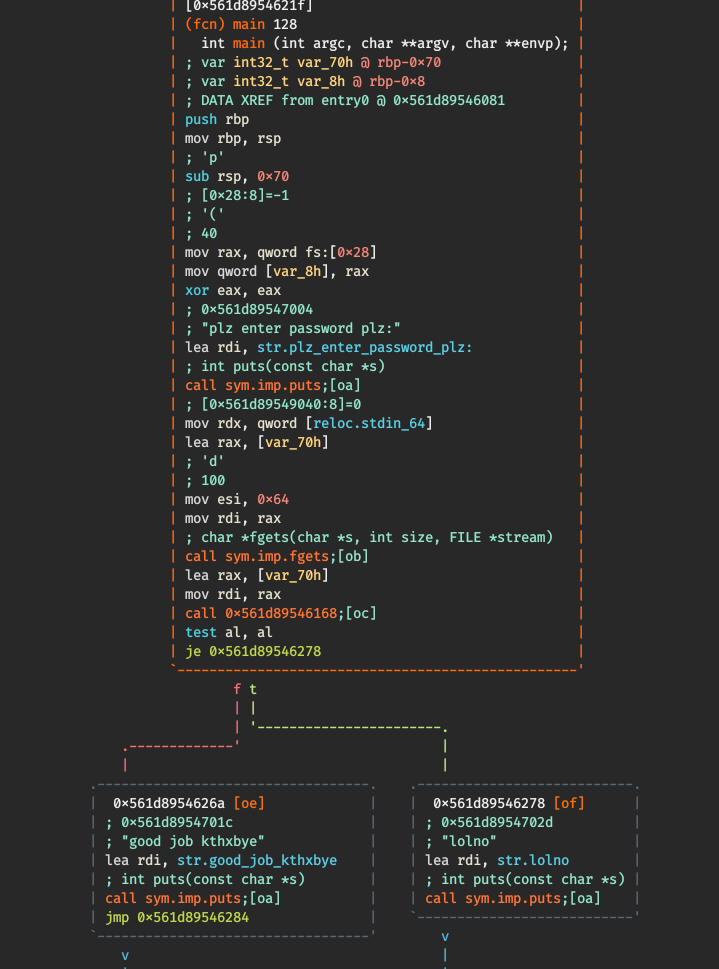
| [0x561d89546168]> pdf
p: Cannot find function at 0x561d89546168
[0x561d89546168]> pd
; CALL XREF from main @ 0x561d89546261
0x561d89546168 55 push rbp
0x561d89546169 4889e5 mov rbp, rsp
0x561d8954616c 4883ec08 sub rsp, 8
0x561d89546170 48897df8 mov qword [rbp - 8], rdi
0x561d89546174 488b45f8 mov rax, qword [rbp - 8]
0x561d89546178 0fb600 movzx eax, byte [rax]
0x561d8954617b 0fbec0 movsx eax, al
0x561d8954617e 89c7 mov edi, eax
0x561d89546180 e8d4ffffff call 0x561d89546159
0x561d89546185 83f865 cmp eax, 0x65 ; 'e' ; 101
,=< 0x561d89546188 740a je 0x561d89546194
| 0x561d8954618a b800000000 mov eax, 0
,==< 0x561d8954618f e989000000 jmp 0x561d8954621d
|`-> 0x561d89546194 488b45f8 mov rax, qword [rbp - 8]
| 0x561d89546198 4883c001 add rax, 1
| 0x561d8954619c 0fb600 movzx eax, byte [rax]
| 0x561d8954619f 0fbec0 movsx eax, al
| 0x561d895461a2 89c7 mov edi, eax
| 0x561d895461a4 e8b0ffffff call 0x561d89546159
| 0x561d895461a9 83f870 cmp eax, 0x70 ; 'p' ; 112
|,=< 0x561d895461ac 7407 je 0x561d895461b5
|| 0x561d895461ae b800000000 mov eax, 0
,===< 0x561d895461b3 eb68 jmp 0x561d8954621d
||`-> 0x561d895461b5 488b45f8 mov rax, qword [rbp - 8]
|| 0x561d895461b9 4883c002 add rax, 2
|| 0x561d895461bd 0fb600 movzx eax, byte [rax]
|| 0x561d895461c0 0fbec0 movsx eax, al
|| 0x561d895461c3 89c7 mov edi, eax
|| 0x561d895461c5 e88fffffff call 0x561d89546159
|| 0x561d895461ca 83f868 cmp eax, 0x68 ; 'h' ; 104
||,=< 0x561d895461cd 7407 je 0x561d895461d6
||| 0x561d895461cf b800000000 mov eax, 0
,====< 0x561d895461d4 eb47 jmp 0x561d8954621d
|||`-> 0x561d895461d6 488b45f8 mov rax, qword [rbp - 8]
||| 0x561d895461da 4883c003 add rax, 3
||| 0x561d895461de 0fb600 movzx eax, byte [rax]
||| 0x561d895461e1 0fbec0 movsx eax, al
||| 0x561d895461e4 89c7 mov edi, eax
||| 0x561d895461e6 e86effffff call 0x561d89546159
||| 0x561d895461eb 83f868 cmp eax, 0x68 ; 'h' ; 104
|||,=< 0x561d895461ee 7407 je 0x561d895461f7
|||| 0x561d895461f0 b800000000 mov eax, 0
,=====< 0x561d895461f5 eb26 jmp 0x561d8954621d
||||`-> 0x561d895461f7 488b45f8 mov rax, qword [rbp - 8]
|||| 0x561d895461fb 4883c004 add rax, 4
|||| 0x561d895461ff 0fb600 movzx eax, byte [rax]
|||| 0x561d89546202 0fbec0 movsx eax, al
|||| 0x561d89546205 89c7 mov edi, eax
|||| 0x561d89546207 e84dffffff call 0x561d89546159
|||| 0x561d8954620c 83f87a cmp eax, 0x7a ; 'z' ; 122
||||,=< 0x561d8954620f 7407 je 0x561d89546218
||||| 0x561d89546211 b800000000 mov eax, 0
,======< 0x561d89546216 eb05 jmp 0x561d8954621d
|||||`-> 0x561d89546218 b801000000 mov eax, 1
`````--> 0x561d8954621d c9 leave
0x561d8954621e c3 ret
|