Writeup: RITSEC 2019 - Random
Information
- category : crypto
- points : 290
Description
nc ctfchallenges.ritsec.club 8001
Writeup
Let’s connect to the server:
1 | $ nc ctfchallenges.ritsec.club 8001 |
The first thing I thought was that the random numbers were related by some
operations modulo 67 because ord('C') = 67.
After at least 10 minutes of trying different tricks on the modulo operation
I gave up and I started reading about random generator and possible attacks
on them.
The most used random generator (not cryptographically secure) is
MT19937.
This is not secure because there are two possible and relatively easy
attack on it:
- If the time is used as the seed of the algorithm, then we can try to
bruteforce the seed. Ex: Try to set as the seed :
time + 1, time + 2,..., time + nuntil the output of the algorithm is
the same as the one in the server. - We can clone the state of the
PRNGif we have624sequencial input,
because the algorithm is linear and can be
reversed
I tried both of the attack but they didn’t work. The second was less probable
of working because we didn’t have 624 sequencial output, so I couldn’t clone it.
After some time I got the idea to see how the rand() function is implemented
in C.
Are you starting to ‘C’ a pattern?
I found various links on stackoverflow/stackexchange and I have seen
the actual implementation on my machine. It wasn’t in the end very useful,
however I learnt something new.
The only thing we have to do at this point, is to try the attack 1.
So I connected to the server and I save the random numbers in an array (seq),
then I tried to bruteforce the seed starting from time(0).
1 |
|
1 | $ gcc finder.c -o finder |
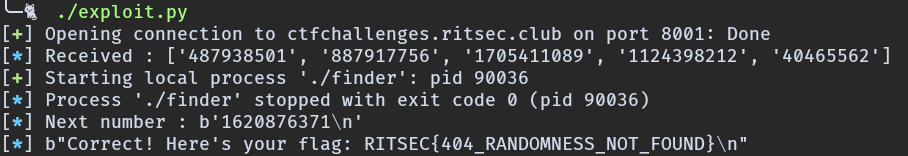
Oh yeah we found it. We could do this operation manually and win the challenge,
but manual solutions are bad, so we can script an automatic
solution to the problem.
Exploit
finder.c:
1 |
|
exploit.py:
1 | #!/usr/bin/env python3 |
Flag
RITSEC{404_RANDOMNESS_NOT_FOUND}