Writeup: DEF CON 2013 - BadMedicine
Information
- Category: web
Writeup
Challenge was available at
http://badmedicine.shallweplayaga.me:8042 where we found a login form:

We tried a simple login and we got to this page:
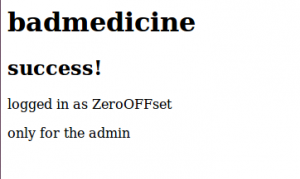
So we were in the right place but with the wrong credentials.
Looking at cookies we found this:
username=32c93a9a8168a1563709
This cookie, seen has hex value has the same number of byte as the inserted username, but ASCII codes is messed up.
So we logged in as "admi", copied the cookie and brute-forced last character with this script:
1 | // Bruteforce to find the 'n' |
And the key simply came up:
Flag
1 | Key FOUND: who wants oatmeal raisin anyways twumpAdby |